I was originally going to write this guide as part of my post on OSINT for e-mail addresses, but really this is better as separate subject.
PGP keys are used for a variety of purposes, but one of the main reasons they exist is to allow someone to verify and protect their online identity. They can be used to digitally sign documents or software, to verify a username or e-mail address, or for encrypting documents. Whatever they are used for, PGP keys are always tied to a username or an e-mail address, so wherever there are PGP keys, there may be snippets of information that are useful for OSINT. This post will show how PGP keys can be used as an information source in OSINT investigations.
Researching usernames and e-mail addresses is a basic task of most OSINT work, but PGP keys can offer additional information to help make links between different entitites in a way that most e-mail and username research methods would miss. For example, public PGP keys are encoded which means that their contents cannot be read by search engines. This means analysing a PGP key can sometimes lead to the discovery of an e-mail address where Google and others fail.
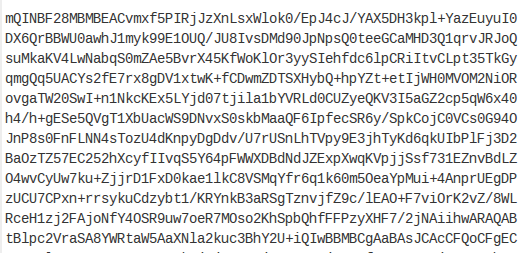
PGP keys used to verify identities in some common dark net markets are also often reused on other platforms and so can eventually be linked to clearnet identities. You can read here how the US and German authorities used PGP keys to link two Darknet market admin accounts to a real-world e-mail address.
These are just a couple of useful examples. If you can find a PGP key, you can find an e-mail address or username, and because PGP keys are unique and used for verification, wherever you find a key, you can be confident it is associated to the same e-mail address or username. The rest of this guide will look at some common places to find PGP keys, how they are structured, and how they can be analysed to extract the username or e-mail address associated to that key.
PeeGeePee.com
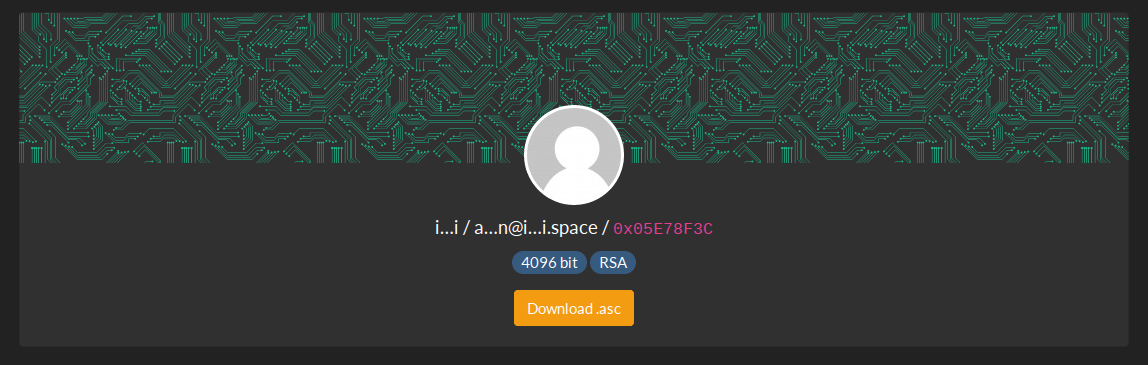
I should be clear at the outset that people who use PGP keys rarely do so because they are up to no good and they want to stay hidden. On the contrary, PGP keys are publicly listed so that people can verify their identities and allow others to send PGP-encrypted e-mail to them, for example. There are many public PGP keyservers, but PeeGeePee.com has a nice clear format that is helpful to explain the PGP key structure. Note that PeeGeePee.com redacts the actual e-mail address associated to the key (and most PGP keyservers do not even show this much information at the outset) – but as OSINT investigators this is the detail that we really want. I’ll show how to extract the e-mail address from a PGP key shortly, but there is some additional information about the PGP key that’s worth noting:
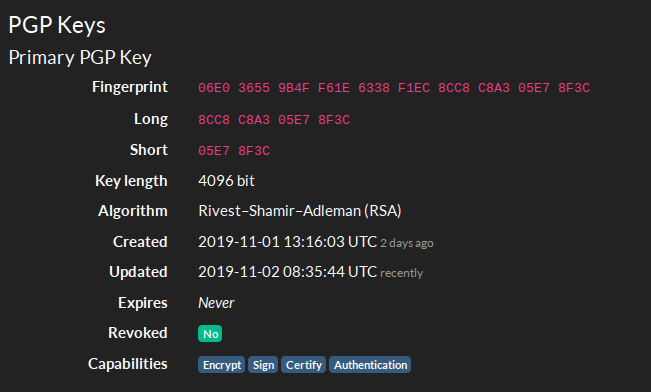
PGP keys each have a unique fingerprint. The fingerprint is derived from the full key and then can be abbreviated further into long and short versions of the fingerprint. These fingerprints make PGP keys easier to share (they fit nicely on your business card, for example), but it also makes them easier to search for across the internet and other PGP keyservers. Note that the fingerprint is often shortened with a 0x at the front followed by 8 hexadecimal characters e.g.0xA1B2C3D4 etc:
The other information confirms when the key was created (which is helpful for building OSINT timelines), that it has not been revoked, and when the expiry date is (although not all keys have expiry dates). We also learn that this key can be used for encryption, signatures, certification, and authentication.
Extracting The E-mail Address From The PGP Key
When you have identified a PGP key of interest, a little work is required to extract the username or e-mail address it is associated to if you don’t have it at the outset. In this example I will combine two built-in Linux commands curl and gpg to download and extract a key of interest.
Curl is built into Linux and Mac OS by default. GPG is also installed in most Linux builds by default, but you’ll need to use Homebrew to install GPG on a Mac. Just to make clear PGP (Pretty Good Privacy) is the type of key/encryption type, GPG (Gnu Privacy Guard) is the software used for managing and creating PGP keys. Confused? You might be.
For Windows there is GPG4Win which will allow you to download and import PGP keys, although I won’t refer to it in this guide. There’s an installation video guide here to get started and this will help you import a public key to determine the e-mail address.
In this example I’m going to use this key here that was chosen completely at random from PeeGeePee.com. It’s expired and so is no longer current, but it can still be used to demonstrate the principle. The file we want to extract and analyse is the .asc file containing the public key. To get the URL right-click on it and copy the link path.
1. Open a terminal and enter the following command. (Ctrl + Shift + V to paste the URL into the terminal).
$ curl https://peegeepee.com/B3889B1D99B288587ADBC2BDCE92C995CC4803BB.asc2. The output will look something like this:
This is the full PGP public key containing the information we want, but it isn’t very useful yet because we can’t read it. This is where GPG comes in. GPG is a program for the creation and management of PGP keys and is usually used for encrypting e-mails or signing software, but because it can decode the raw PGP public key blocks, we can use it when we want to find which username or e-mail address is linked to the PGP key of interest.
To make this work in the command line, it is possible to use a pipe (|) to take the output of the curl command and instead of printing the full PGP key into the terminal, we can pass the result of the curl command to gpg so that it will read the key for us and tell us what the associated e-mail address is.
3. The command is as follows:
$ curl https://d.peegeepee.com/B3889B1D99B288587ADBC2BDCE92C995CC4803BB.asc | gpgThis gives an output like this:
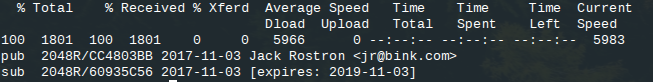
Now we have the name of the person and the full e-mail address associated to the PGP key! Notice that Google found no matches for this e-mail address because it cannot easily index public PGP servers:
When a PGP key is associated to a username instead of an e-mail address, this command returns data in the same way except with the username in place of the e-mail
Time for a real-world example…
Keybase – Unmasking Script Kiddies
Keybase.io is a very popular public PGP key server. It’s almost a social media platform in it’s own right. User have followers, links to profiles on other platforms, a list of how many devices they have associated to a particular key, as well as a profile picture (although not always). Here’s the Keybase.io profile for one of my favourite infosec Tweeters Leslie Carhart:
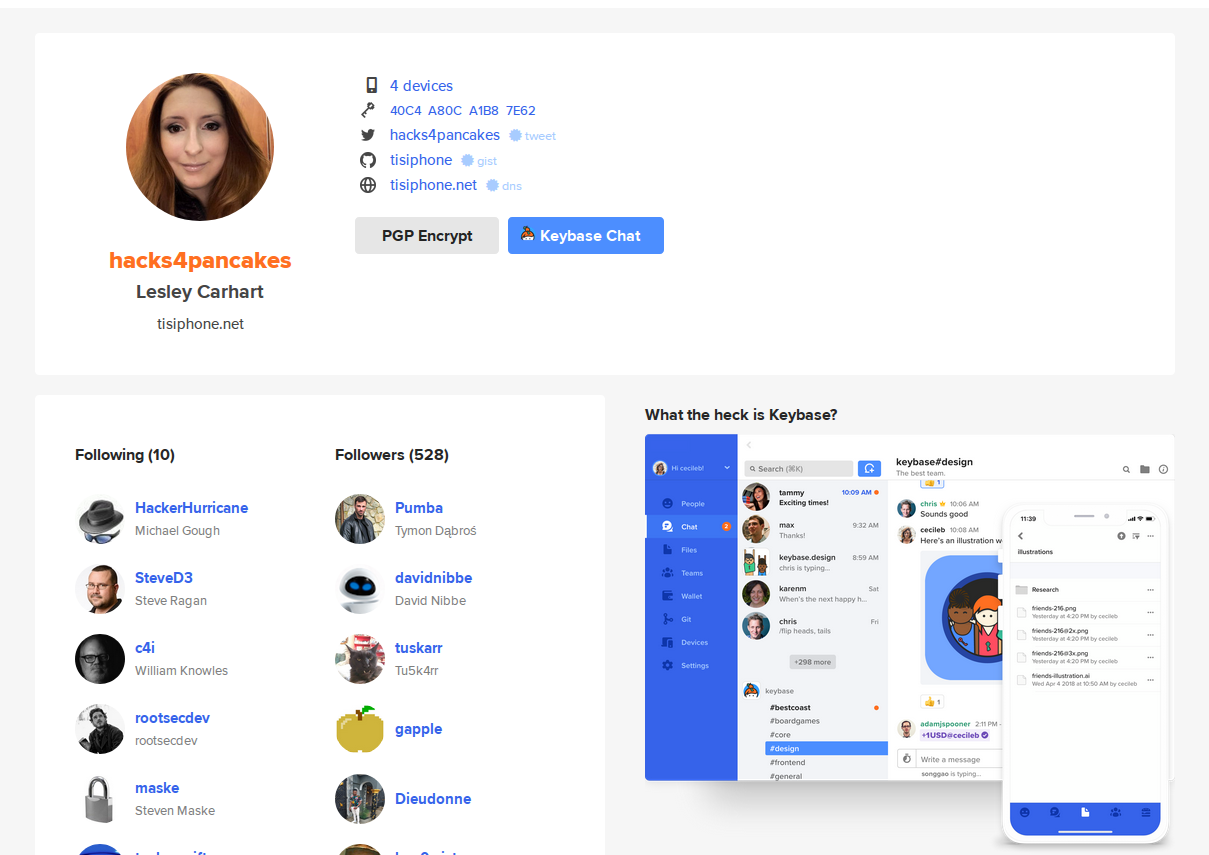
Notice that the user’s e-mail address is not listed in the bio and so cannot be readily indexed by search engines. It is necessary to download and extract the e-mail address from the PGP key in a similar way to the example above.
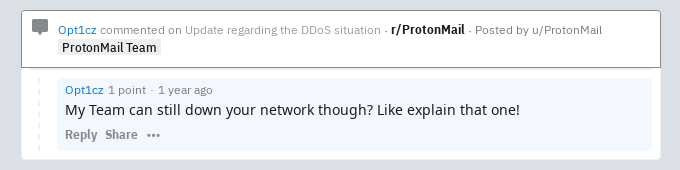
To show how this can be useful for OSINT, I’ll show how it was possible to help verify the identity of a careless script kiddie who used the moniker Opt1cz when he launched a DDOS attack on Protonmail last year. When Protonmail posted a situational update on Reddit, a user called Opt1cz posted a reply to thread claiming that he and his gang were responsible for the DDOS attack:
His only other Reddit post was when he posted in the Reddit KeybaseProofs forum:
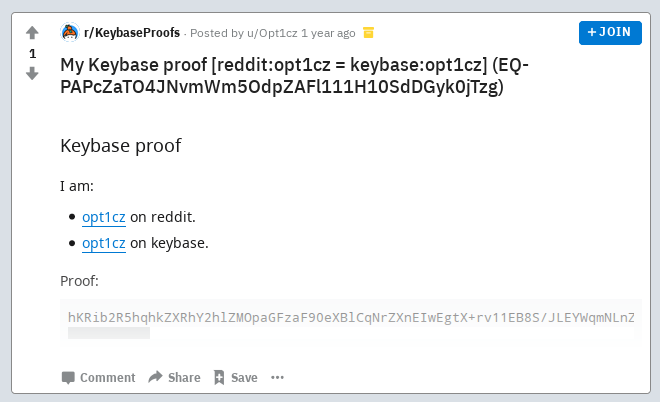
He helpfully provides a link to his Keybase profile:
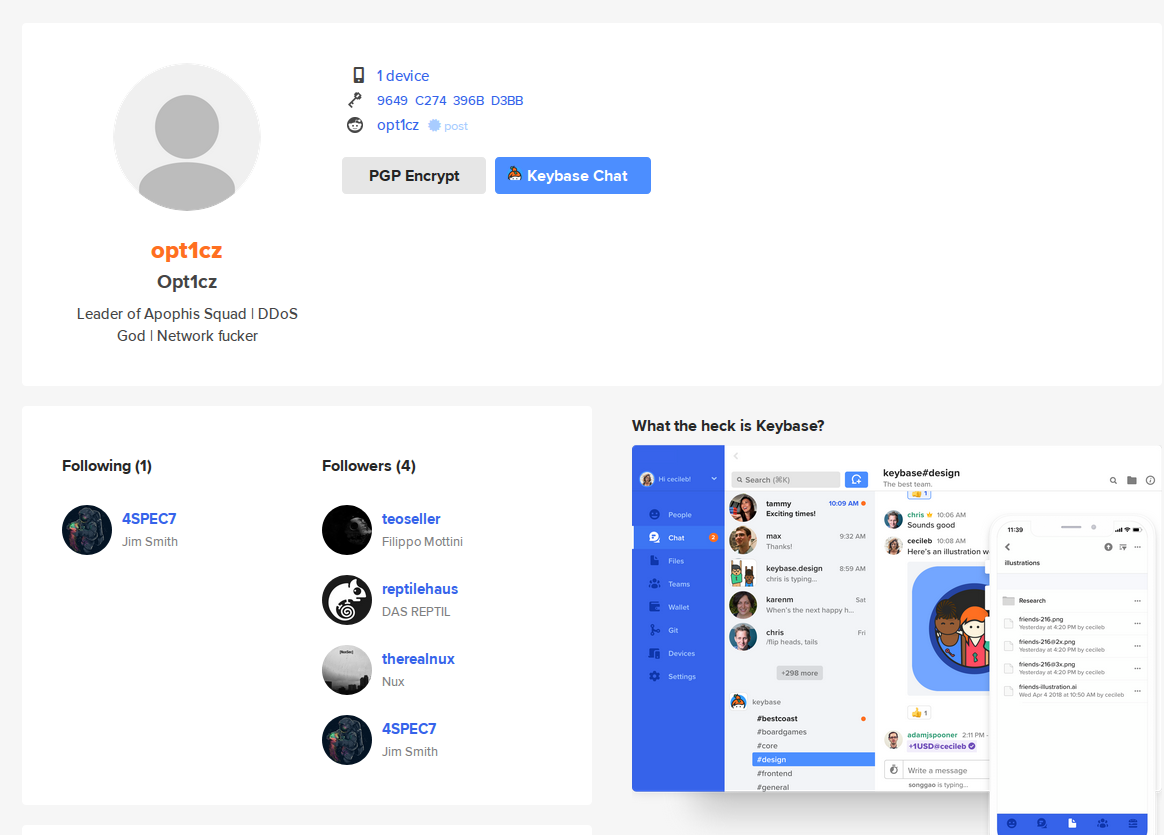
It would be helpful to know his e-mail address, and this can be obtained by the combination of curl and gpg as demonstrated above. The URL for a keybase PGP key is always in the following format:
curl https://keybase.io/username/pgp_keys.ascIncidentally this also means that when you’re doing a username search, you can always try the target username on Keybase and then try to work towards an e-mail address using this method.
To find out what Opt1cz’s e-mail address is, use the following command:
$ curl https://keybase.io/opt1cz/pgp_keys.asc | gpgThis gives the following output in the terminal:
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 3165 100 3165 0 0 5178 0 --:--:-- --:--:-- --:--:-- 5171
pub 4096R/396BD3BB 2018-07-01 opt1cz <[email protected]>
sub 4096R/5A61C24C 2018-07-01 [expires: 2034-06-27]So from this we learn what his e-mail address is – very useful. Of course because he has identifiable followers on Keybase, it would be possible to find their e-mail addresses and usernames too and begin to build a better picture of his online associates.
Just in case there was any doubt as to the OSINT vlaue of a PGP key, Keybase even provides a helpful graphic to show how a user’s key is linked to their social media accounts AND their own hardware:
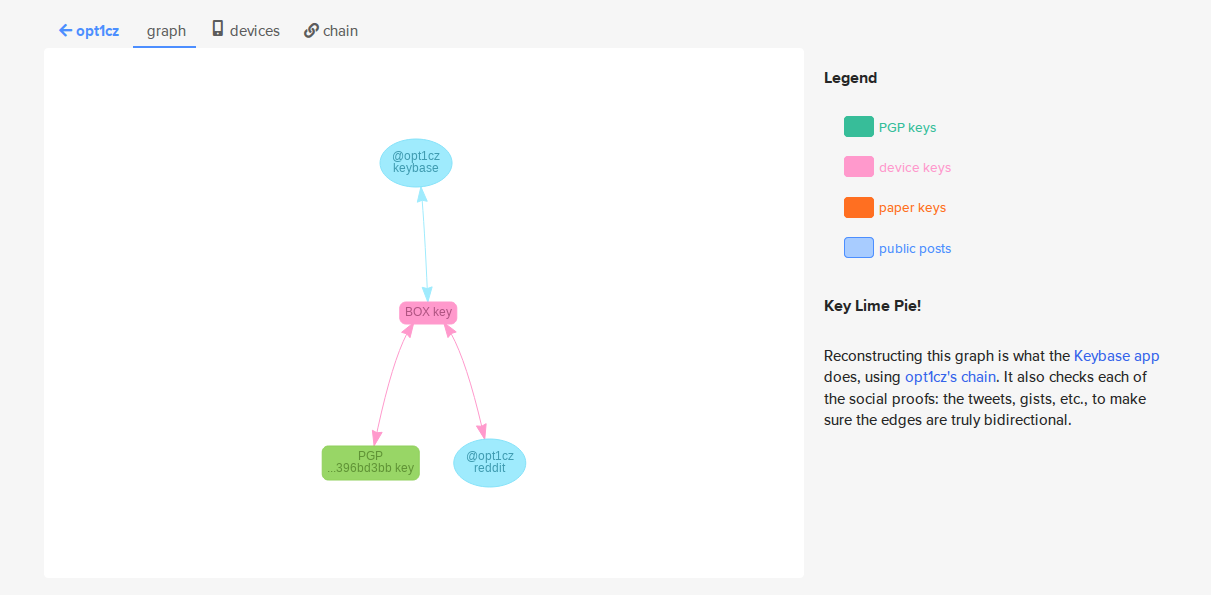
In case you’re thinking would someone really be stupid enough to DDOS their own e-mail provider? The answer is yes, he really was that stupid and is now serving three years in prison for his troubles.

PeeGeePee.com is gone. do you have an alternative site?
Some of these might be useful:
https://alternativeto.net/software/peegeepee/
would this work on a partial PGP key?
Good question – I’ve never tried it. I think the only way to know for sure is to try and see.