In my last post on Reverse IP Lookups I wrote about the challenges OSINT investigators face when it comes to attributing a website to someone. Reverse IP lookups show which other domains are hosted at the same IP address, which is often (but not always) an indicator of what other websites your subject controls. This gives you a wider collection of information to sift through than would have been possible with one domain alone.
This post will continue from where the last one left off and will show the challenges and the possibilities that CloudFlare brings to OSINT work.
At the end of the last article I did a reverse IP lookup for the Far-Right domain stormfront.org. The results showed several other domains that shared the same IP address, which offers some additional insights into the wider organisation and people associated to it:
derekblack.com
stormfront.com
whiteheritage.com
whiteprideenterprises.com
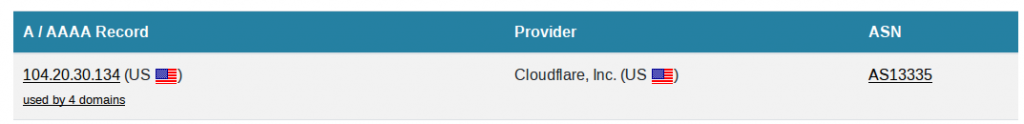
The IP where these domains are hosted is 104.20.32.134, which is owned by CloudFlare. CloudFlare are one of the largest providers of network services anywhere on the internet. Their huge infrastructure means that those who choose to use CloudFlare to protect their websites enjoy really high levels of availability (but not always) and really effective DDOS protection, amongst other things.
For OSINT purposes, this can make digging into a domain slightly more challenging. If we do a reverse IP lookup for a website protected by CloudFlare, we only really see the information presented by CloudFlare – the real IP address is usually somewhere else, but locating this true IP address can yield a lot of additional information.
There are two popular tools that can be used to do this. One with a GUI (though in my experience, it is less effective), and one based in the command line.
Crimeflare
Crimeflare was founded because its creator objected to the way in which CloudFlare allowed its services to be abused by criminals, spammers, and other internet undesirables who made use of CloudFlare’s protection to continue their operations unhindered.
Crimeflare works on the basis that since all sites hosted behind CloudFlare need an SSL certificate, it is possible to use the SSL certificate to find out more information about associated websites. SSL certificates can be expensive so CloudFlare often allows one SSL certificate to cover multiple domains, so by finding domains that share a common SSL certificate, it is theoretically possible to see domains that may have been registered at roughly the same time by the same person.
As a quick example I’ve used the domain truck-mobiles.de:
Querying this domain with Crimeflare shows that this domain shares an SSL certficate with lots of other sites:
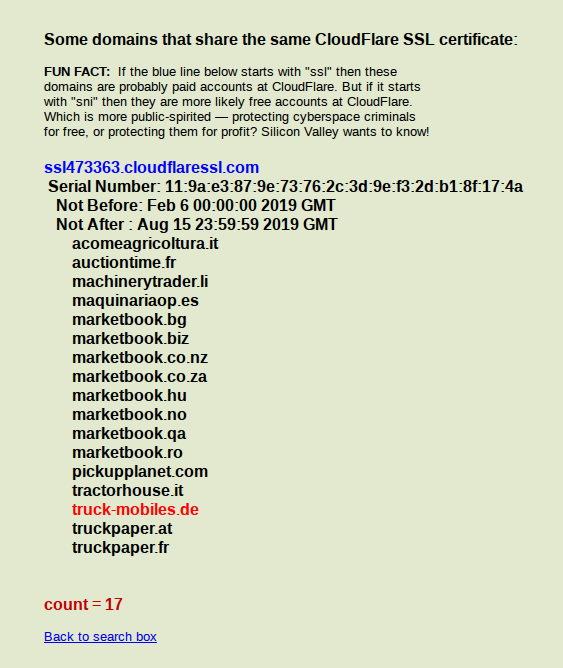
So from a single query into one domain, there are now an additional 16 domains linked by a shared SSL certificate that are probably linked to or owned by the same person. This can be extremely useful for OSINT purposes.
Crimeflare is a simple tool with a basic GUI but as always it is important to be aware of its limitations when compared to other tools. For a more in-depth look at SSL certificates for OSINT purposes I recommend reading this OSINT.curious article by Sector035.
CrimeFlair
Cloudflair is a very powerful but simple tool to find out about a domain that makes use of Cloudflare. It works on a similar basis to Crimeflare, but gives a much richer picture. I’ve blogged about it before here but it’s worth highlighting its features in a bit more detail.
Cloudflair queries the target domain to find out the details of the SSL certificate, but then it uses the power of Censys to find out which other IP addresses are currently presenting the same unique SSL certificate to the internet. This means that not only does it identify the IP address used by Cloudflare, but it finds any other IP address on the internet that is presenting the same certificate, i.e. the domain’s true IP address. Once the real IP address is identified, it’s possible to carry out further reverse IP searches to find out more about the domains that we’re doing OSINT on.
Installing CloudFlair
To use CloudFlair it’s necessary to create a Censys account (free) and obtain an API key and an API secret. I wrote a previous blog post about how you can install it here.
To run the CloudFlair python script from within the CloudFlair directory use the following command:
python3 cloudflair.py mytargetname.comTo make using CloudFlair a little more convenient, it’s possible to create an alias in the Linux command line. To do this enter the following:
sudo nano .bashrcScroll to the end of the file and add the following:
alias cloudflair='cd ~/CloudFlair && python3 cloudflair.py'Ctrl + X and Y to exit. Restart your terminal for the changes to take effect. Now to use CloudFlair enter the following:
cloudflair stormfront.orgOr without creating an alias:
python3 cloudflair.py stormfront.orgThis is what Cloudflair looks like when it’s pointed at stormfront.org:
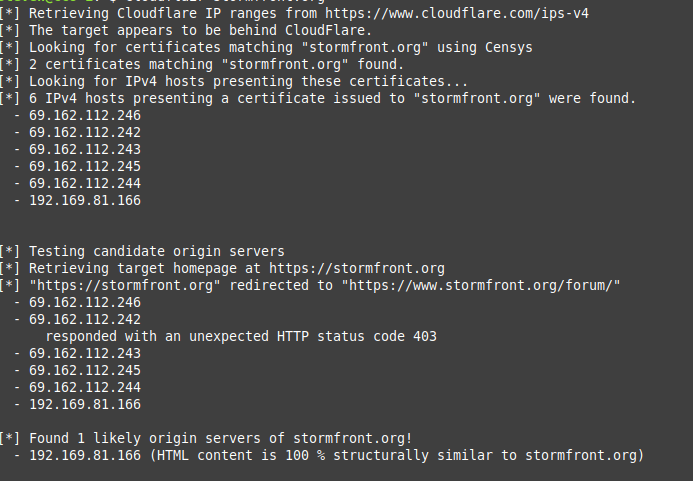
It’s already clear that CloudFlair is finding a lot more information than Crimeflare did. As it looks at the SSL certificate presented by Cloudflare, it uses Censys to find other IP addresses presenting the same identifical SSL certificate. This means it is possible to see beyond the IP presented by CloudFlare and the “real” IP that the domain belongs to. In this case Cloudflair brings back six extra IP addresses that are associated to the stormfront.org domain. CloudFlair also gives us some useful extra information – the HTML content of the stormfront.org website hosted on Cloudflare is 100% identical to the website hosted at 192.169.81.166. HTML similarity is another useful OSINT method that I’ll write about in the near future.
To look into this new information further, we just need to repeat the same reverse IP lookups as before. SecurityTrails throws up some interesting results:
First of all there are some new domains associated to these IPs that we didn’t know about up until now:
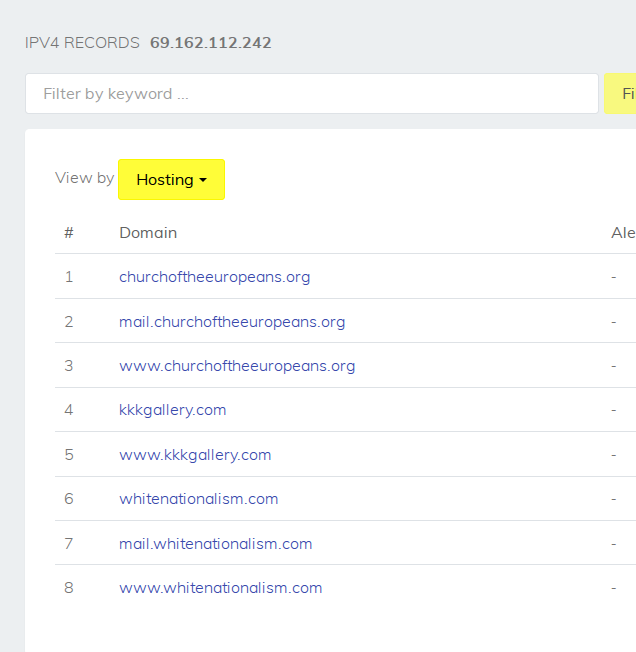
Then investigating one of the other IP addresses that Cloudflair found throws up another surprise:
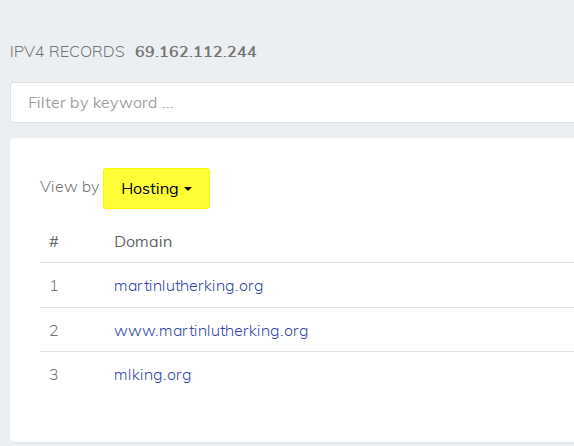
Yes, you read that correctly. By starting with a simple reverse IP lookup to learn about stormfront.org, not only have we discovered several new IP addresses and other associated domains, it turns out that one of the domains is martinlutherking.org.
Using the Internet Archive we can see that martinlutherking.org was in existence as far back as April 1999. This is what it looked like then:
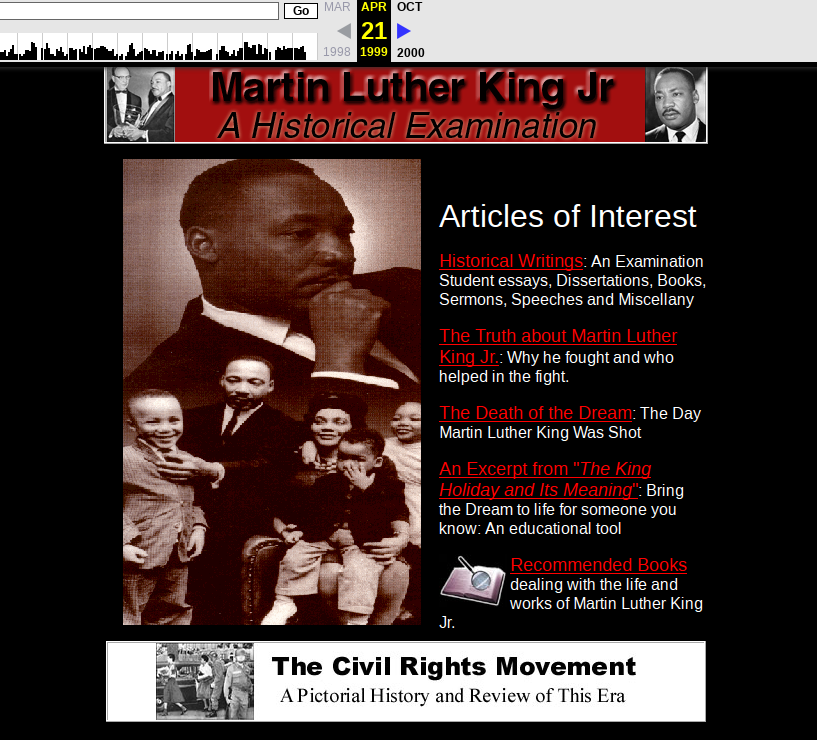
On the surface it looks quite innocuous, but inside it is full of white supremacist material – exactly the kind of information that we would expect to associate with Stormfront. This is not a new revelation of course, since it the association between Stormfront and martinlutherking.org has been known for a few years, but this does demonstrate the OSINT potential of reverse IP lookups and digging a little deeper into domains that share the same internet spaces. Having started with a single domain of interest, this method has identified many new domains that were not explicitly linked before, as well as some new IP addresses to work with. It also offers insights into some of the people and behaviours of the subject group.

So what does the shared Cloudflare SSL cert across these different domains really mean then?
Randomly clustered domains by Cloudflare? = no connection
Same cloudflare user account? = same domain/site admin
Domains moved behind Cloudflare around the same time? = possibly same site admin, but may just as well be totally unrelated
Is there a way to find out?
Jim,
I’m don’t think there’s a certain way to find out in every case and often there is no connection between domains sharing the same cert. However some domains that are clustered together (as in the Crimeflare screen cap above) are mirrors/aliases of each other and share a lot of content in common. It suggests either the same owner and/or that they were added to Cloudflare at the same time. These would then become pivot points for you to explore further to see if you can enhance what you know about the original target domain.
Use crimeflare quite some time ago but it was good.
For reverse IP lookup I’m using https://ip-ninja.com/