The term “OSINT” sometimes gets thrown around a little too loosely. The “open source” part of OSINT is straightfoward enough: there’s a world of information out there and with enough digging and practice you can find almost anything you could ever think of – but by itself this is not OSINT. The “intelligence” part of OSINT is often neglected, sometimes with quite serious consequences. Getting your hands on the data you want is usually easy enough, but this raw information has to be analysed and turned into a coherent narrative, a process that is often fraught with difficulty and uncertainty.
A lot of uncertainty can be removed if there is a clear plan in place at the start. We have to remember that OSINT is never done simply for its own benefit. It is always part of a wider objective like a journalistic investigation, or a missing person case, or a military operation, and so on. The nature of the objective that you’re doing OSINT for will ultimately determine the scope and shape of the research that you undertake, and the findings that you provide to your client or boss. Collecting raw information from the internet is easy enough, but turning it into an organised, verified, and useful report takes a little more work.
The Intelligence Cycle
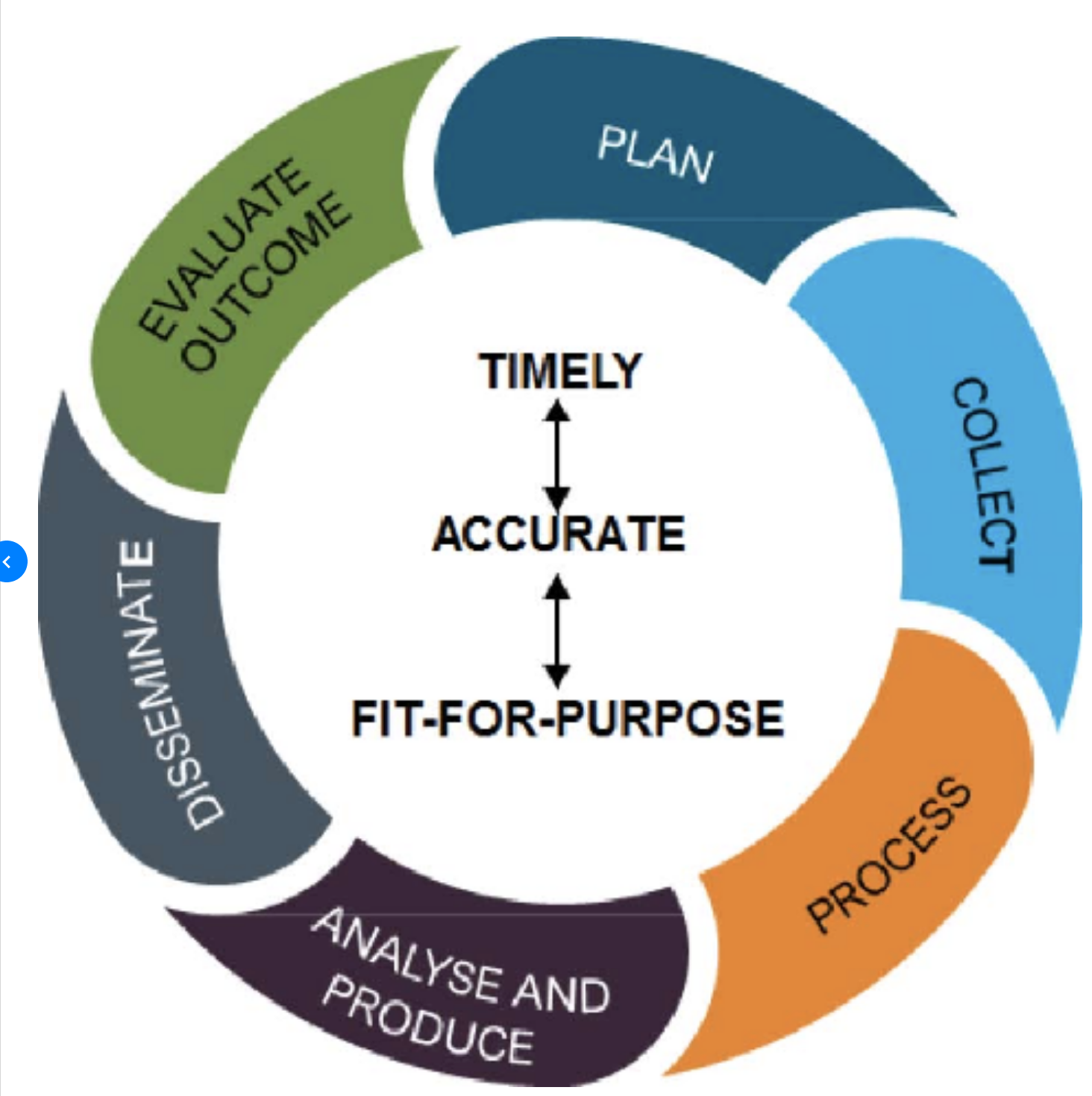
To ensure consistency and thoroughness in OSINT work most organisations adopt a version of the Intelligence Cycle like the one pictured above. There are several variations of this model, but they are all very similar. They all assume an initial plan or goal, followed by a collection phase, some processing and analysis, and finally dissemination of the information to the intended recipient. The processing and analysis phase is the most important one because this is where the raw collected data is critically evaluated, theories are tested, and correct information is separated from the false or ambiguous (with varying degrees of success).
This means that “here’s a bunch of stuff I found on the internet” is not OSINT. It might be open source, but it isn’t useful intelligence until it’s been tested, verified, and analysed. Does the information you found provide useful answers to the question you set at the start? Have you verified it? How have you dealt with the conflicting information you collected? How much weight have you given to sources of information that are of uncertain reliability? Have you provided you client with OSINT or BULLSHINT? And so on.
Is Antifa.com Controlled By Russians?
So what has all this got to do with Antifa? I actively try to avoid politics on Twitter, but sometimes it’s inescapable despite my best efforts. Recently my interest was piqued by a claim that the domain antifa.com was redirecting visitors to Joe Biden’s presidential campaign site, and that furthermore, the Antifa website was registered by shady Russians. Was this the spectre of electoral interference about to make a reappearance?
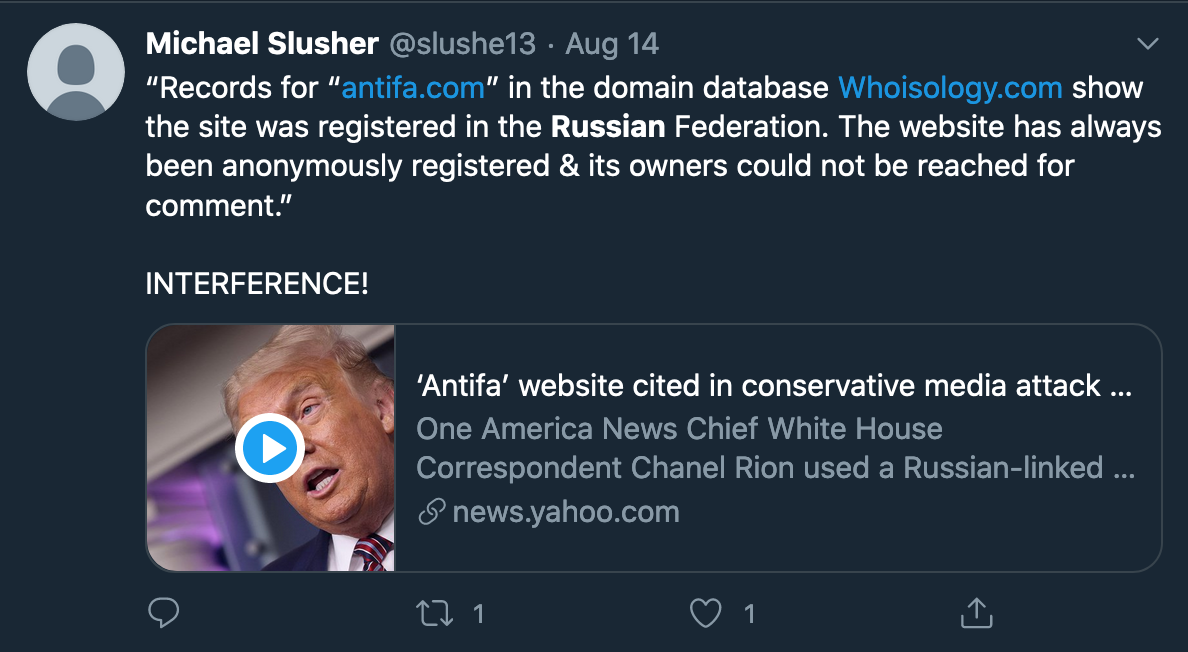
The central claim about a Russian link seemed to revolve around the WHOIS history of the Antifa.com domain – I’m always initially sceptical about claims made solely on the basis of WHOIS since it’s such an ambiguous source of information, but I decided to dig into the domain history a little more to see what it was possible to find out. What follows is a brief step-by-step guide to using the Intelligence Cycle to plan a little OSINT research and analysis to see what we can find out.
Planning – What Do I Actually Want To Find Out?
This is quite a simple query. I could ask “Was the redirect from Antifa.com to Joe Biden’s website a Russian plot?” It’s a sensationalist question, but it’s also a closed question (you could only answer “yes” or “no”). It’s almost a leading question too, in that your political stance might cause you to come to a conclusion based simply on how the the question is asked, and not necessarily based on any of the research.
Closed and leading questions are not good investigative questions. Open questions are much better and less likely to feed our biases. A better question to ask might be “What is the nature of the relationship between Antifa.com and it’s Russian registrar, if any?”
Collection – Find The Materal That I Need
The collection part of the intelligence cycle is where we can gather all the information that we need to try and answer the question we set at the start. In this case I want to know about the history of the antifa.com domain, who owned it, what content it has displayed over time, and what we can find out about any redirects that are in place.
To do this I’m going to collect information about the server (so I can catch any redirect information that might be present), the WHOIS history, the certificate history, and any preserved content from the Wayback Machine that might show me what content the site has displayed over time.
1. Server Information
Curl is still my favourite tool for quickly grabbing information about a server. To grab information about the Antifa.com server, I entered the following command:
$ curl -I http://antifa.com
The -I flag ensures that I get server header information back. In this case I get the following result:
HTTP/1.1 302 Found Server: nginx Date: xxx Connection: keep-alive Location: https://itsgoingdown.org/ X-Served-By: Namecheap URL Forward
This is interesting because there’s still a 302 redirect in place, but now it points to a different URL. We can also see that Namecheap’s URL Forwarding service is in place, so I’ll grab some information about how that works to add to my analysis later:
2. WHOIS History
I also want to know as much as I can about the WHOIS history. After all, this is the source of the suspicion that there might be some Russian links to the site. There are several tools to do this. RiskIQ and Whoisology both have WHOIS data going back to 2012/2013. However we know that the domain was registered at least as far back as 2002 (and as it turns out, even before that) so we need to go further back if possible. It’s possible to pay for a service like this with Domain Tools, but a full historic WHOIS report is a bit too pricey for a single blog post.
Fortunately there is a little hack that takes advantage of the fact that WHOIS records are themselves often archived by the Wayback Machine, so we can use this technique to find WHOIS records that go back as far as 2009:
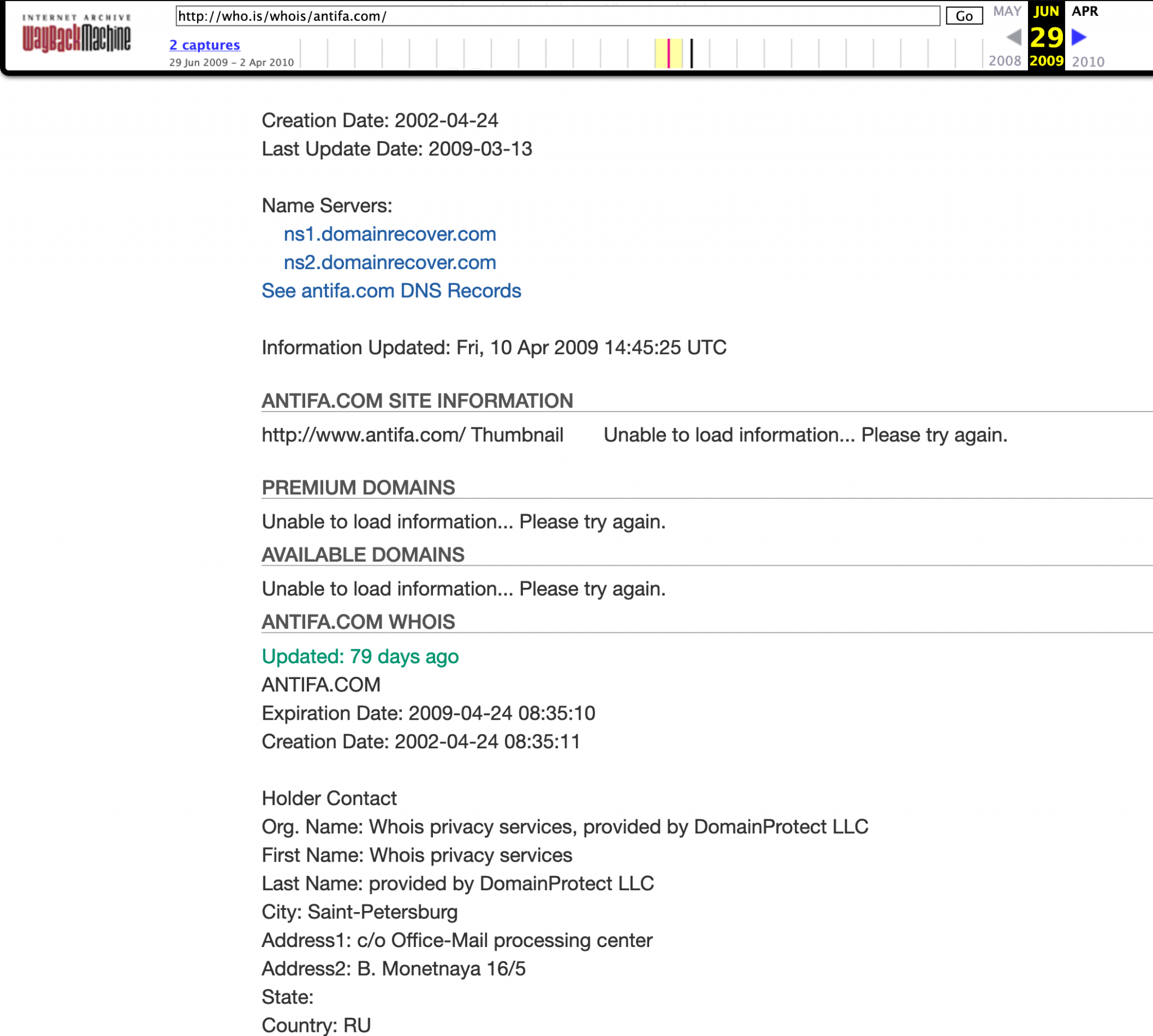
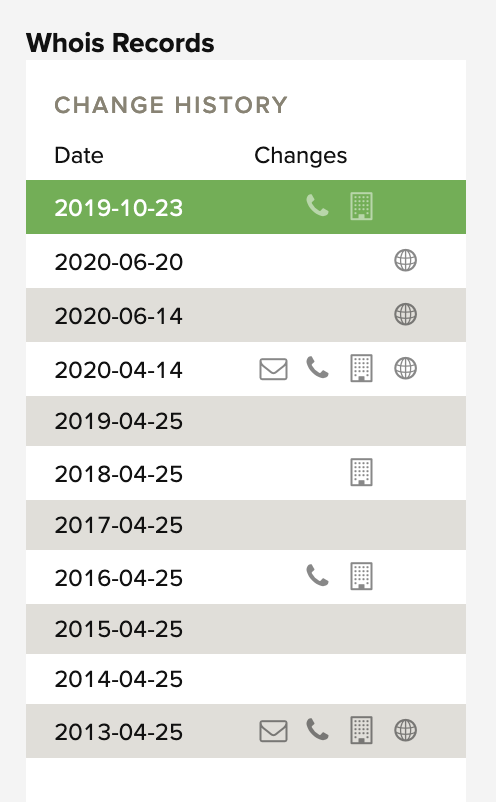
It’s not ideal but that’s as far back as we can go without splashing the cash on a paid-for WHOIS record. The information held by RiskIQ helpfully lists more recent registration renewal or change dates:
3. Certificate History
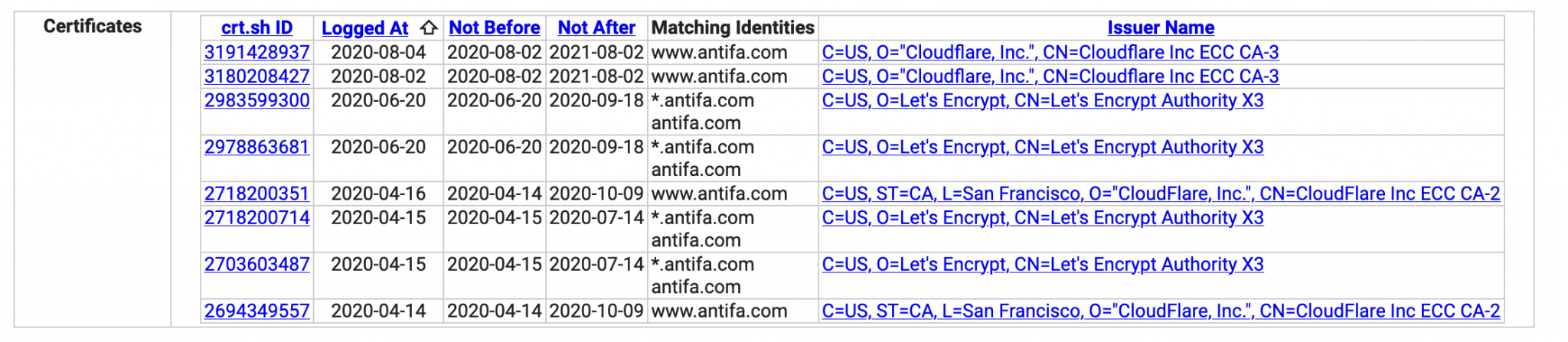
A domain’s certificate history can offer several insights into its structure and setup, including ownership and hosting changes. Crt.sh offers a nice clear overview of a site’s certificate history, and there’s always Censys if you need to go into more depth. Here’s the very short certificate history for Antifa.com:
4. Wayback Machine
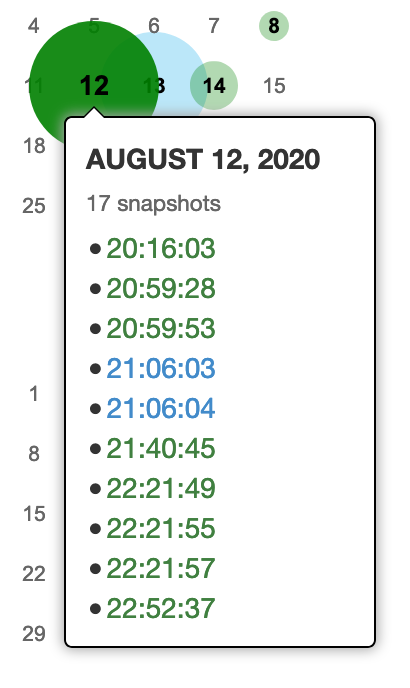
Fortunately the subject domain has been archived many times over the years. The oldest capture is as far back as January 1999 and the most recent was 17th August 2020. It’s no coincidence that so many snapshots have been made since the domain begain to be heavily publicised in the last week:
 With this information we’ll be able to look at the historical content of the website to see what it was displaying at different time periods.
With this information we’ll be able to look at the historical content of the website to see what it was displaying at different time periods.
Processing & Analysis
Because this is just a short example for a blog post, I’m not going to spend much time doing any processing of the information I’ve collected. Ordinarily it’s usually helpful to turn raw data into spreadsheets, graphs, and relational diagrams to make analysis easier, especially with more complex tasks.
Instead I’m going to move straight on to analysing the raw information that I collected. My aim is going to be to try and construct a timeline from the WHOIS, Certificate, and Wayback Machine history to try and see how the domain has changed over time and what that might mean for the original question about the domain and the relationship with its Russian registrar.
Before doing that I want to look at the server header I grabbed at the start:
HTTP/1.1 302 Found Server: nginx Date: xxx Connection: keep-alive Location: https://itsgoingdown.org/ X-Served-By: Namecheap URL Forward
The HTTP 302 code tells us that all requests to visit antifa.com are all now directed to another site, itsgoingdown.org. This site does in fact appear to be a left wing political website, which is what we might expect. This redirect is enabled through Namecheap’s URL forwarding service, so by looking up Namecheap’s documentation about how this process works, we can infer that the person(s) managing the Antifa.com domain does so via Namecheap’s control panel and that the domain is therefore managed through Namecheap.
This shouldn’t be surprising because this is exactly what the current WHOIS records tell us:
Domain name: antifa.com Registry Domain ID: 85915752_DOMAIN_COM-VRSN Registrar WHOIS Server: whois.namecheap.com Registrar URL: http://www.namecheap.com Updated Date: 2019-10-23T14:38:04.00Z Creation Date: 2002-04-24T12:35:11.00Z Registrar Registration Expiration Date: 2021-04-24T12:35:10.00Z Registrar: NAMECHEAP INC Registrar IANA ID: 1068 Registrar Abuse Contact Email: [email protected] Registrar Abuse Contact Phone: +1.6613102107 Reseller: NAMECHEAP INC
Ever since 23rd October 2019, the subject domain has been registered with Namecheap. So where’s the Russian registrar link that we were interested in? If we go back through the historic WHOIS data we can see that between 2009 (the oldest WHOIS data we can access) and the switch to Namecheap on 23rd October 2019, the domain was registered to an address in St Petersburg, Russia:
Registrar Abuse Contact Phone: +7.8129140281 Domain Status: clientUpdateProhibited Domain Status: clientTransferProhibited Domain Status: clientDeleteProhibited Registry Registrant ID: Registrant Name: Whois privacy services provided by DomainProtect LLC Registrant Organization: Whois privacy services, provided by DomainProtect LLC Registrant Street: c/o Office-Mail processing center Sadovaya, 53 Registrant City: Saint Petersburg Registrant State/Province: Saint Petersburg Registrant Postal Code: 190068 Registrant Country: RU Registrant Phone: +1.8662452838 Registrant Phone Ext: Registrant Fax: Registrant Fax Ext: Registrant Email: [email protected]
I think this was the point at which Yahoo! News and several others decided to end their research and go straight to publishing. This was a little premature though:

Hmm. That’s a very broad definition of the word “linked”. This is what happens when rushing from Collection to Dissemination and skipping over the Analysis part of the Intelligence Cycle. Russia is a country – what’s the link to the registrant? When did they control the domain? Can we know what they did with it? Do they still own it? All these questions need to be resolved before we draw a conclusion. Better to be slow and right than fast and wrong.
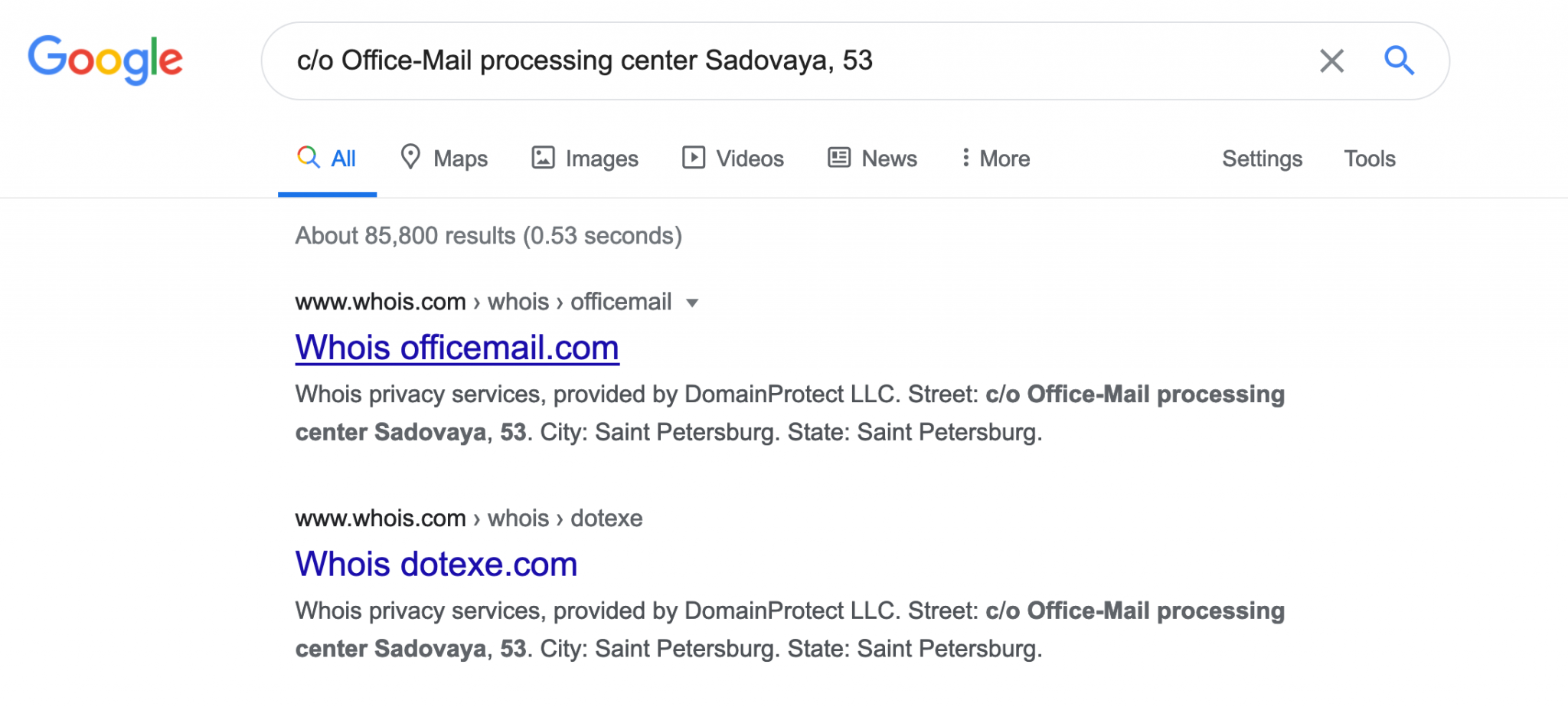
So what exactly is the link to Russia in the WHOIS data? The registrant name and e-mail are hidden in the WHOIS records, but the street address is not. By searching for the address “c/o Office-Mail processing center Sadovaya, 53” we can see that it’s linked to hundreds and hundreds of other WHOIS records for other domains.
Why might this be? Fortunately the Wayback Machine records we saved during the collection phase will help. We can see what Antifa.com looked like during the time it was registered by a mysterious Russian organisation. Brace yourselves for the big reveal…
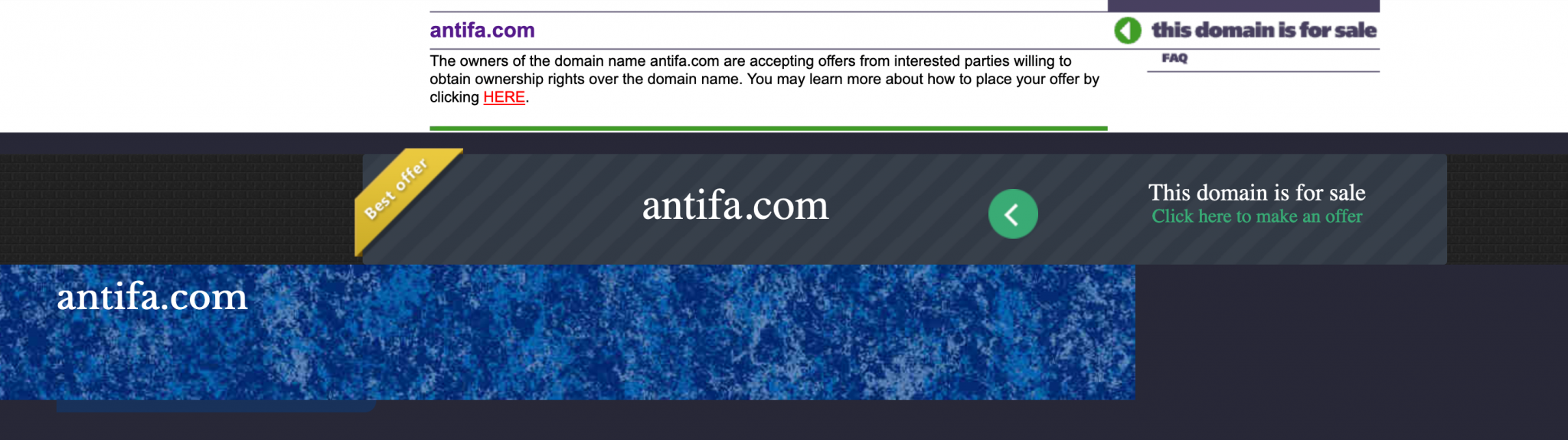
For the entire time that the domain was owned by the shadowy Russian group, all they did was offer it up for sale. Although we don’t have WHOIS records older than 2009, we can see that even in 2008 the domain was parked and up for sale. In fact it was for sale for many years up until it switched to a new owner on 23rd October 2019.
Even after the change of ownership, no significant content changes were made until 14th April 2020. We can see this in the certificate history from crt.sh.

The antifa.com domain never had an SSL certificate before 14th April 2020. This date is significant because it’s also the same date that the Antifa Website Twitter account was created:
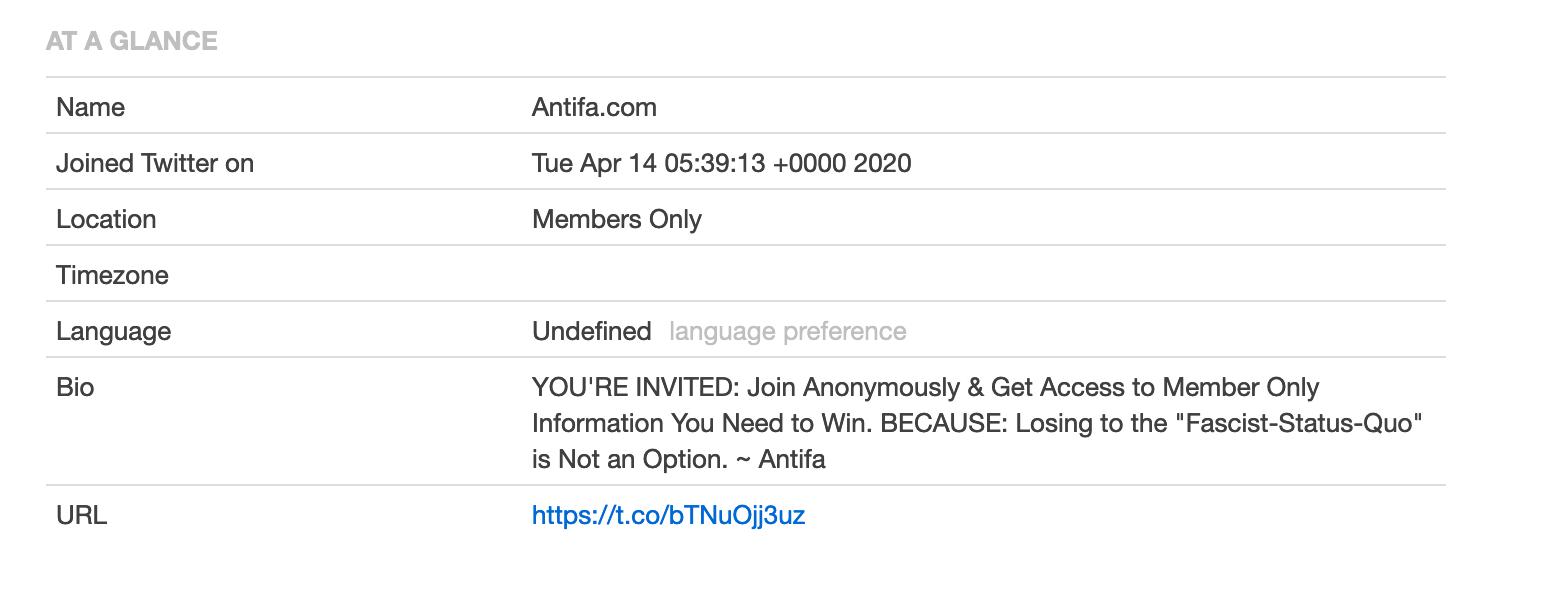 (Of note the URL in the Antifa Website Twitter bio also redirects to itsgoingdown.org. )
(Of note the URL in the Antifa Website Twitter bio also redirects to itsgoingdown.org. )
The Antifa.com YouTube channel was also created at around this time, on 18th April 2020:
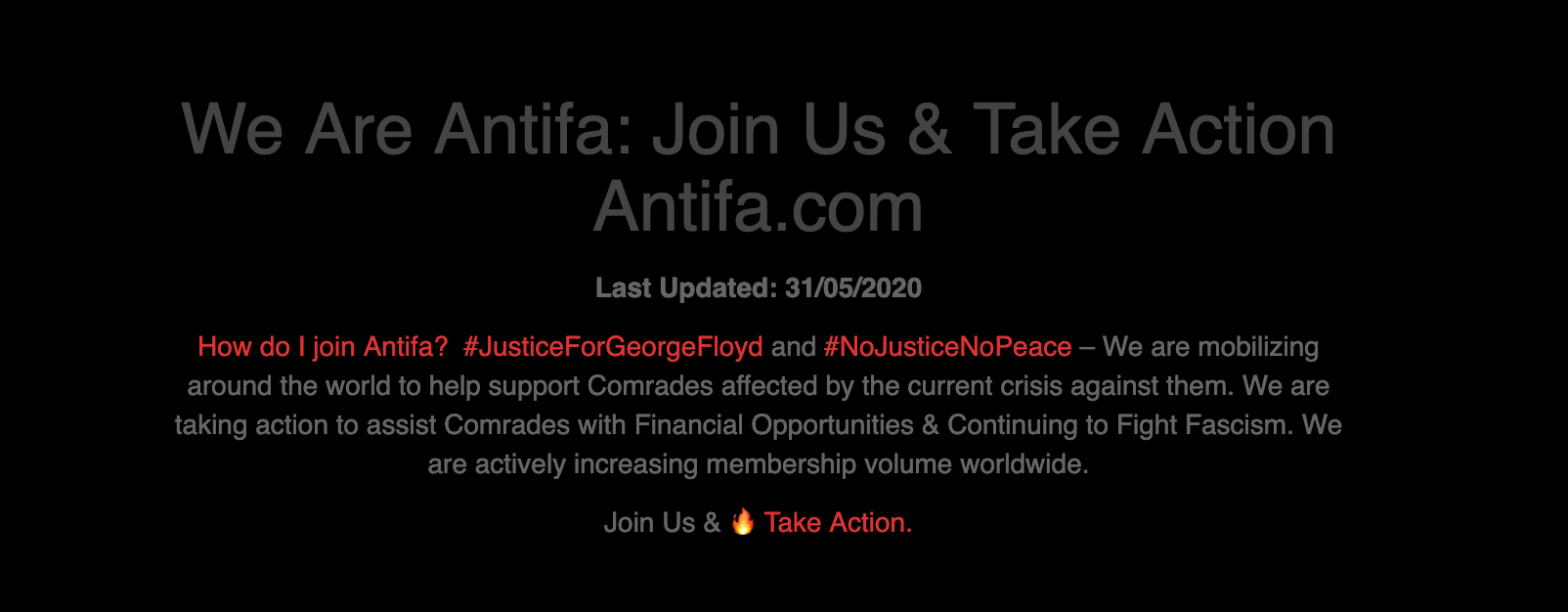
Sure enough, the first Wayback Machine capture after 14th April 2020 reflects this change. The “For Sale” sign is gone and has been replaced with new content:
Remember that at this point the previous Russian registrar has not been linked to the site for over eight months. This was still the case on 12th August when the domain was set up to redirect to Joe Biden’s website:
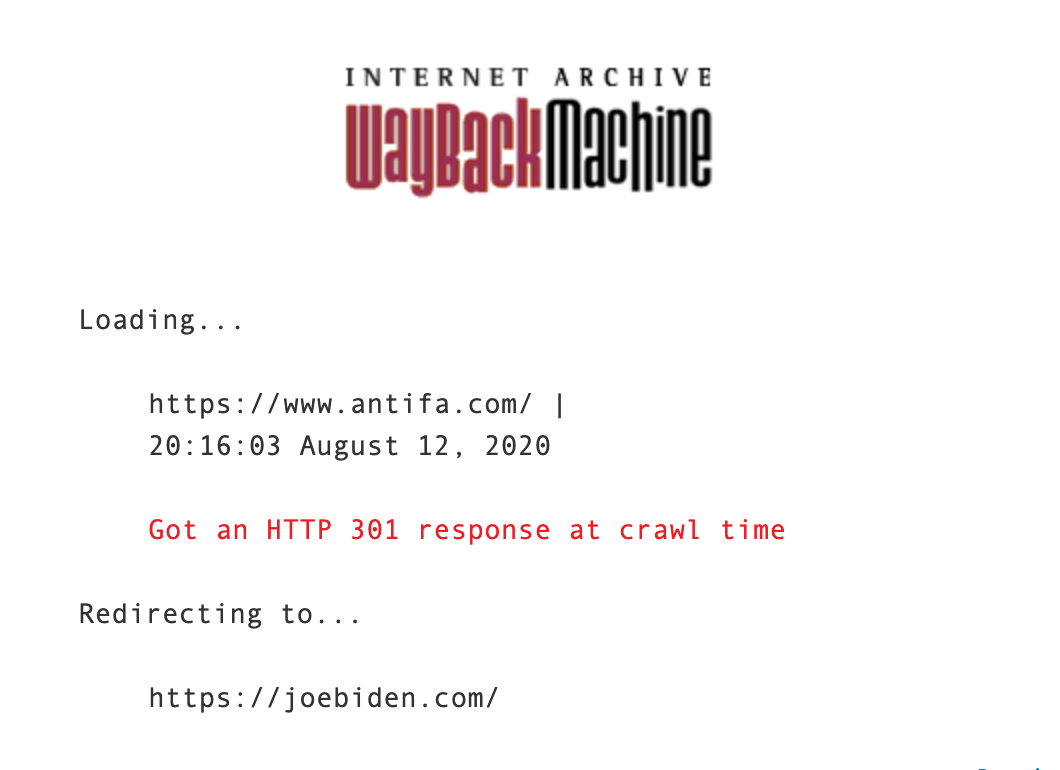
Can we be confident of a link between Russia, Antifa, and Biden based on what we’ve found in our limited research? I’m not sure we can.
Product Dissemination
Because this is just a short blog exercise, there’s no one to disseminate the information to beyond you, the reader (well done if you’re still reading this far on). It’s a good point at which to review our original question and see if the collection and analysis we’ve done actually answers the original question – what is the nature of the relationship between Antifa.com and its Russian registrar, if any?
This has been quite a brief exercise and there are certainly an awful lot of other avenues of research we could have gone down. So what can we conclude? The world of OSINT is rarely black and white and there will always be some areas of uncertainty. There’s nothing wrong with a little uncertainty, provided that this is reflected in your findings: your conclusions always have to be supported by your research and not embellished.
Based on this research we can say that the domain was previously registered by a Russian-based organisation and has been since at least 2009, possibly even before that. We can also say that during the Russian registrant’s period of ownership the evidence suggests that the domain was only parked and offered for resale. There is no evidence to suggest any content was hosted on the domain during their ownership period, or that any redirects were in place. The registration of the domain changed in October 2019 and there is no clear connection to the Russian registrant after that point. The current owner of the domain uses Namecheap as a registrar but from the information collected it is not possible to say who they are. The current owner has used the domain for a distinctly different purpose than the previous Russia-linked owner. At the time the domain was configured to redirect traffic to Joe Biden’s website almost 11 months had passed since the last clear association to any Russian entities. The evidence collected tends not to support the suggestion that the diversion of traffic from Antifa.com to Joe Biden’s website was linked to the previous Russian registrant.
So if you’d cut the corner in the intelligence cycle and gone straight from Collection to Dissemination you could easily have missed the important details and made the sensational – but unsupported – assumption that the diversion of traffic from Antifa.com to Joe Biden’s campaign site was a Russian scheme. It’s certainly tempting to take shortcuts and draw exciting conclusions, but this rarely makes for accurate reporting.

While this post feels like BullshINT, going from collection to dissemination, I wanted to help fill a couple of the collection gaps, since I have access to a paid Domain tools account. I reviewed the historical companies through a paid account. The goal of posting was to share more collection information. I don’t think it will change the analysis, just trying to help.
When looking at the whois history section from 2002 to 2008, the whois record had the Organization listed as Eruobox in St. Petersburg. The record changed to the c/o Office-mail information on 2008-08-15.
When reviewing the screenshot history, it shows that in 2009 the site was used for pharma sales on a web page called “Indian Drugs.” The screenshots are tagged 2009-07-31 and 2009-10-04. On 2009-12-14 it is back to the for sale style pages. The whois records from that time still show the c\o Office-Mail.
Thanks for the extra info Ray. There’s really no subsitute for Domain Tools when it comes to historic WHOIS records!
Thanks for sharing your insights!
A wealth of information. It will time to digest all.
Thank you.
This was a very good read, I followed the process and it opened my eyes
You were correct in the calling post bs. They fabricated the Russia link. It doesn’t connect to Russia anywhere in any of domain research sites. So they not only responded to a fact with misinformation /lies. They did what all media now feels way to comfortable doing. They lied. The site is linked to
Kalkofnsvegur 2, Reykjavik, Capital Region, 101, IS