Counting Crowds In Public Spaces
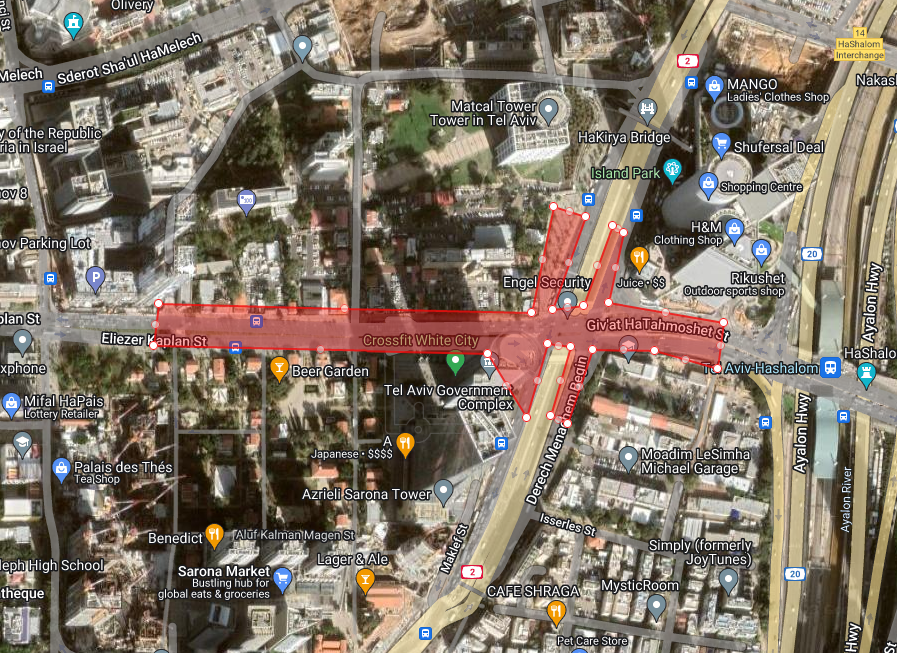
This week’s huge protests in Israel drew huge crowds to the streets – but how many people took part? Crowd sizes are often used as evidence to show how widely supported a particular cause is, so being able to determine how many people took part in a demonstration is an important skill for those working […]
Counting Crowds In Public Spaces Read More »