A common challenge for OSINT practitioners and penetration testers alike is to fully identify the range of domains owned and managed by a particular organisation. Identifying the main domain that a company owns is usually fairly easy since it can be found in the second half of a company email (user@example.com) or as part of the main company website (www.example.com) – but what about all the other domains a company manages? How can we find the domains used by subsidiary companies, or intended for future projects, or for parts of the company we don’t know about, and so on?
There are a few techniques that can do this but they come with limitations. Using WHOIS data to find domains registered by a particular company is one technique but the low quality of some WHOIS data and the increased use of privacy services has made this technique much less reliable. Shared hosting can also show common links between domains but while this method can be very accurate it can also be wildly misleading as well. So what other options do we have?
What Is Azure AD?
The growth of cloud services means that many parts of an organisation’s infrastructure that used to be kept hidden away on company premises is now hosted remotely. This means that some of the information about these services can now be discovered through reconnaissance in a way that was not always so easy in the past.
Microsoft still dominate the world of enterprise IT, and at the core of every Microsoft setup is Active Directory. Active Directory (AD) is used to manage groups, users, policies – and domains – in a Microsoft environment. Now that more Active Directory services have also begun to move to Microsoft’s Azure cloud platform, OSINT researchers can leverage these services to attribute domains to a particular organisation with a very high level of confidence without relying on inconsistent WHOIS or hosting data.
Say Hello To AADInternals
The ability to discover this information has been around for quite a while, but it hasn’t always been that accessible. Penetration testers have been using a variety of tools like AADInternals to perform this kind of reconnaissance, but unless you’re handy with Powershell then accessing this kind of data has been hard to do. Worry no longer though because the creator of AADInternals Nestori Syynimaa has released a web-based OSINT tool that leverages AADInternals to make domain reconnaissance much easier and more accessible than before.
In the rest of the post we’ll look at how to use AADInternals to research a domain, and how we can make sense of the results.
Investigating bbc.co.uk
We’re going to try and find out which other domains are owned and managed by the BBC. We know that their main domain is bbc.co.uk but we want to find as many of their other domains as we can. AADInternals lets us query a domain either by Tenant ID (more on this below), domain name, or email address. Note that the email address does not have to actually exist. As long as the domain part (@bbc.co.uk) is correct it does not matter what the username is.
(Note: It’s important to be clear that this tool only works with domains that use Microsoft services. If the company you are researching does not use Microsoft for their infrastructure then you will not find any results. There’s also no simple direct equivalent to this method for other cloud services like Google Workspace either, since Active Directory is unique to Microsoft.)
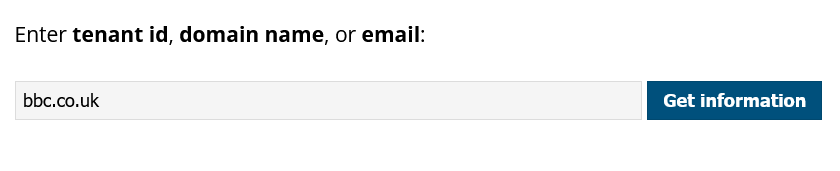
Enter the domain bbc.co.uk into the search box and click Get Information. After a few moments your results will appear. We’ll discuss what they mean below.
Tenant Name and Tenant ID
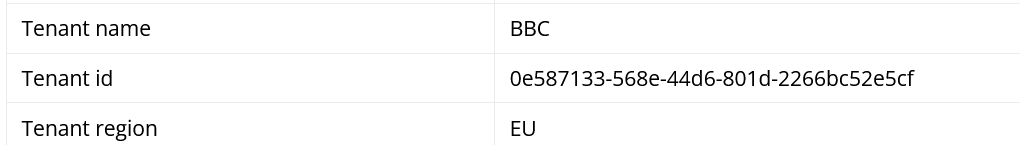
When an organisation creates an Azure instance it is known as a Tenant. Each Tenant has a name and a globally unique identifier (GUID) known as the tenant ID. All the domains that an organisation manages via Azure AD will be associated to their tenant ID. This means that when a domain is linked to a tenant ID in this way we can highly confident that the domain is owned and controlled by organisation.
Tenant Region
This is the primary region the organisation chooses to have its Azure instance.
Default Domain

When first creating an Azure instance, it is necessary to set up a default fallback domain for use within Azure AD. This will always be a unique value followed by onmicrosoft.com. It also can’t be changed once created.
Verified Domains
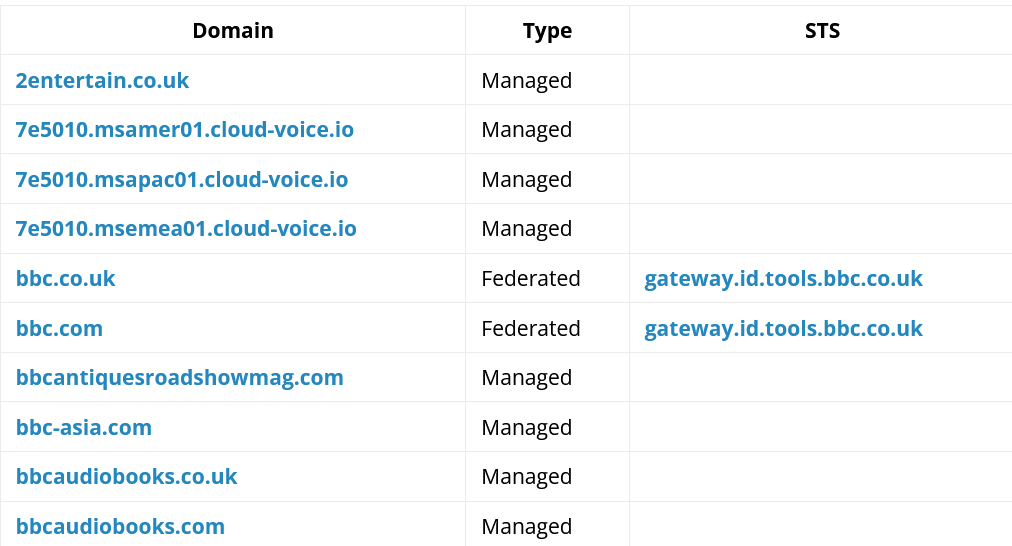
This number lists the total number of verified domains that an organisation is managing within the Azure AD instance. It is a useful and highly reliable indicator. In this case we learn that the BBC are managing a total of 44 domains with Azure AD. So having started with just bbc.co.uk, we can now say witha high degree of confidence that they also control 43 other domains.
The AADInternals web based tool only shows details for the first 20 results, although all the verified domains are listed. If there are more than 20 domains you’ll need to run AADInternals in Powershell and use the Get-AADIntTenantDetails function to find all the verified domain details.
Domain Details
Each verified domain has two other data fields associated to it that can yield useful information. The Type field describes how users log in to their accounts for the domain. If a domain is federated then it means that users are still using an on-premises AD server to handle their logins. On the other hand if a domain is managed then it will not rely on an on-premises AD server to handle user logins. As a general OSINT rule of thumb (and there are plenty of exceptions) if a large organisation like the BBC has a mix of federated and managed domains, the federated domains are more likely to be the primary, older domains. It’s still important to try and verify this, for example by looking at when domains were first registered or first published DNS records.

Some domains may also have an STS entry, like the two BBC domains shown below. STS stands for Security Token Service and indicates that the organisation is using a third-party identity provider to manage user logins. The link in the STS field points directly to where organisation’s users can log in.
AADInternals makes identifying the domains owned and controlled by an organisation very straightforward and does so with a high degree of reliability. If you’d like to dig into this topic a little further I recommend reading this blog post by the creator of AADInternals, Nestori Syynimaa.
