How do you identify the people or group who run a website? Knowing who really owns or controls a domain is an important part of many online investigations, but it can be very hard to do in cases where people do not want to be identified. The quickest and easiest way to find out who owned a particular website used to be through a WhoIs lookup. It was (and occasionally still is) possible to see the name, address, and contact details of the registrant.
In reality it is a long time since this was a reliable OSINT method. It is possible to register a domain anonymously, or even with false details. The introduction of GDPR in 2018 also meant that anonymising the registration details of websites registered in the EU became mandatory. The end result is that now WhoIs lookups are of less value than they were in the past, and this is unlikely to change much in the future. It doesn’t mean that WhoIs enquiries shouldn’t still be part of OSINT basics, it’s just that they aren’t as rich a source of information as they once were.
A Disclaimer
With any method or technique it is important to be aware of its limitations. Short of getting search warrants and subpoenas it can be really difficult to be absolutely certain about who really owns or controls a domain, so it is necessary to recognise that most methods of finding out additional information about a domain are imprecise and can even be completely wrong when looked at in isolation. It is always important to gather as many pieces of information about your subject as possible and then try and verify them from separate sources before committing to any conclusions.
Why Reverse IP Lookups Are Useful
What is a reverse IP lookup, and how is it helpful to OSINT investigators? Reverse IP lookup can provide a lot of information about where a domain is hosted and which other domains are squeezed into the same little bit of internet space. This is often a good way to identify domains that are owned by the same person and so build a bigger picture of their web presence.
A little networking knowledge helps to explain why reverse IP lookups are useful. Every domain on the internet has to have an IP address so that traffic can be routed to it. You want to connect to a website, so you enter www.myfavouritewebsite.com into your browser. Your computer needs to know which IP address to send the request to so you can view the website, so it asks a DNS server which IP address www.myfavouritewebsite.com is currently hosted at. The DNS server checks and tells your computer that www.myfavouritewebsite.com is located at IP address 45.67.131.18*, and it then makes the connection from your computer to that IP address.
There’s one main problem with this way of connecting to different domains. The way that IPv4 addresses are structured means that there are only 4.3 billion possible IP addresses. This was not a problem when the current IP system was invented in the early 1980s, but it is a huge problem now because there a lot more than 4.3 billion servers, routers, phones and other devices that need an IP address to be able to connect to the internet.
For websites one of the solutions to this problem was to make it possible for many domains to be hosted at a single IP address. For OSINT purposes this means that one person or group who own multiple domains will often host them on the same IP address, and so it is possible to begin to make associations between different domains by looking at clusters of domains that share a common IP address.
Reverse IP Tools
There are a lot of tools available that can be used for Reverse IP lookups. A few popular ones are:
Most of these tools have a free element, but limit the number of searches or require you to pay to access a full set of results.
Example #1 – Osintcuriou.us
I’ve started with a really bad example of what can be learned from a reverse IP lookup. I’ve done this deliberately so that it’s possible to see the limitations of this method in that it is not always possible to infer associations from domains that share the same IP. In this example I’ll show what can be learned about the domain osintcurio.us.
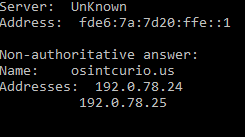
First it is necessary to find the IP address of the domain you want to look at. There are several ways to do this. Any of the sites listed above will show the IP address. In this example I’ve used SecurityTrails but it also possible to find the IP address for a domain in the Windows command line by using nslookup. In the terminal simply type:
nslookup osintcurio.usThis will produce a result like this:
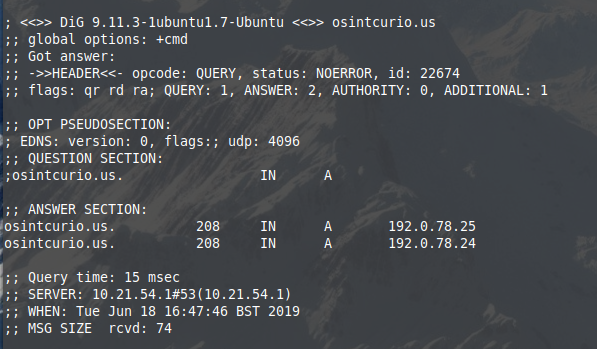
And in the Linux terminal there's a similar command:
dig osintcurio.usWhich gives the result:
If you're not comfortable with command line it isn't an issue - all the sites listed above will tell you the IP address for a domain via a web interface. In this case ViewDNS gives the same result with a GUI:
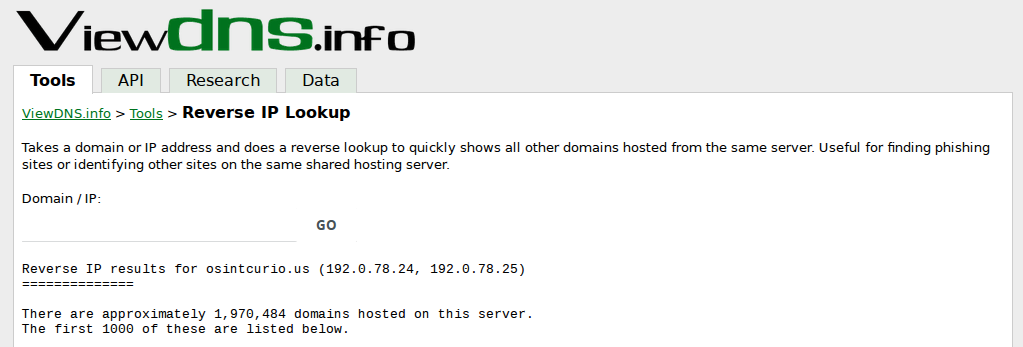
All these results tell us that osintcurio.us is hosted at IP 192.0.78.24 and also 192.0.78.25. Now using Security Trails it is possible to see all the other domains hosted on the same IP:
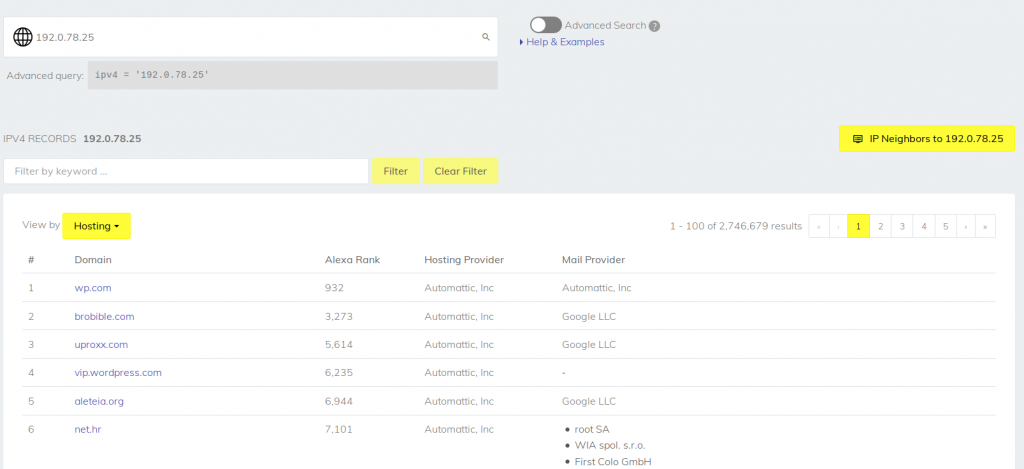
There's a slight issue here. There are 2,746,679 different domains sharing the same IP address. In this case the only conclusion that can be drawn about the associations between these domains is that they use the same hosting provider! I've used this as an example to show that reverse IP lookup is not always useful as an OSINT tool, and that it is important to be aware of its limitations. Let's look at some better examples.
Example #2 - Phishing Domains
Criminals are constantly creating domains designed to make their phishing e-mails look that little bit more credible - all in the hope that you'll be fooled into clicking on the link that installs their malware, or that you'll be tricked into entering your Google password details into a site that's really controlled by hostile actors who want to steal your stuff. It's a never-ending arms race between criminals who create domains for phishing, and security companies who identify them and blacklist them.
Phishtank is a constantly updated list of newly-identified phishing domains, so I'll pick one at random to conduct a reverse IP lookup on.
I've picked amerewards.net. A quick WhoIs check shows that - unsurprisingly - the registrant has chosen to remain anonymous. So is there anything that a reverse IP lookup can tell us about any other sites this person might control? I used DNSLytics to query the IP address and conduct the reverse lookup.
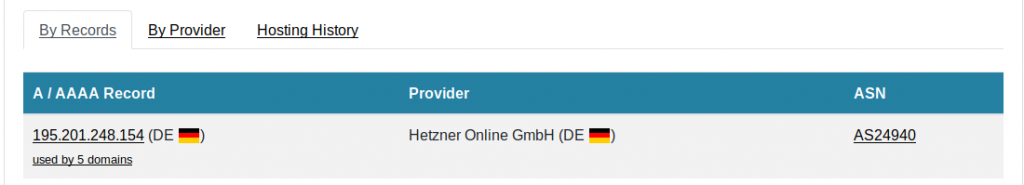
This tells me that amerewards.net is hosted by Hetzner Online GmbH in Germany. More interestingly, it also shows that five other domains share the same IP. Let's have a look at what they are:
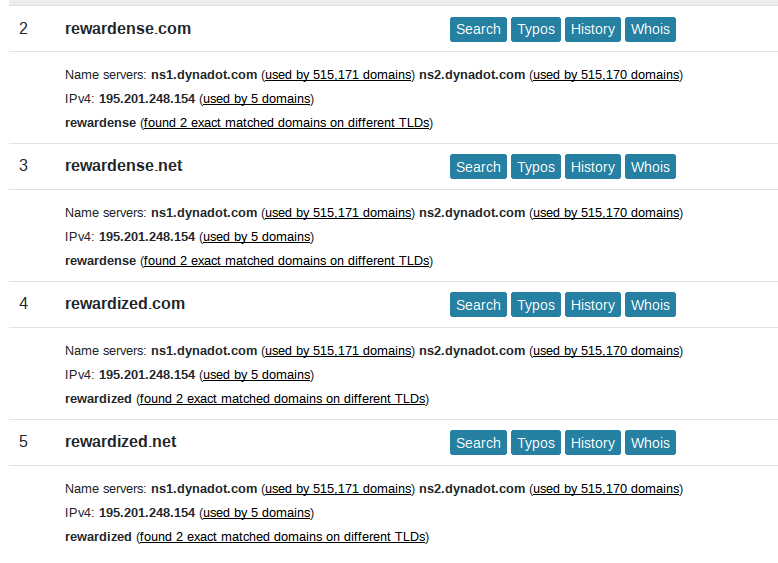
A WhoIs lookup shows that all these domains were registered on the same date, and the reverse IP lookup shows they are all hosted at the same IP address. On the balance of probabilities, it's logical to conclude that they are most likely controlled by the same person. The names of the domains all tend to suggest that they could be used for phishing. Sure enough, visiting one of them causes Firefox to panic:
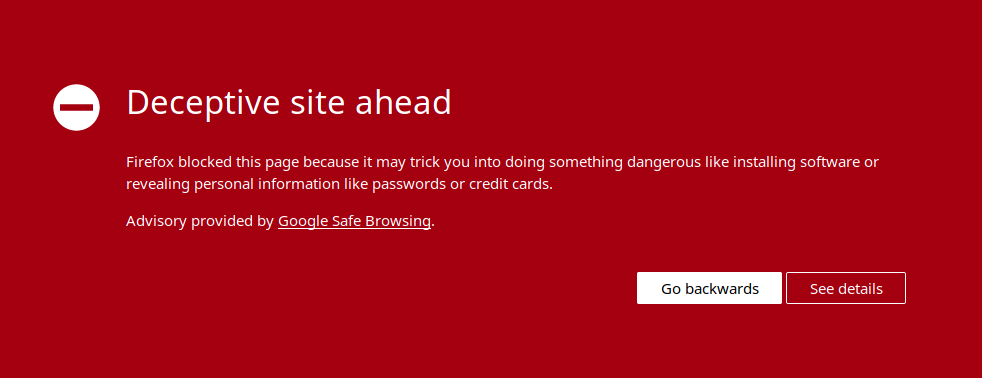
So one of these domains has already been flagged as a phishing site, but at the time of writing, not all of them had been. This shows that from one quick reverse IP domain enquiry, it is possible to quickly identify several more simply by IP association. There are lots of good commercial tools that automate a lot of this kind of work for threat intelligence purposes, but working through it manually gives an idea of how it works.
Example #3 - A White Supremacist Site
Reverse IP can also help to establish associations for more traditional types of investigation into individuals and organisations. In this example I've used the US white supremacist site Stormfront. Repeating the same process as above gives us the IP address where Stormfront is hosted, 104.20.32.134.
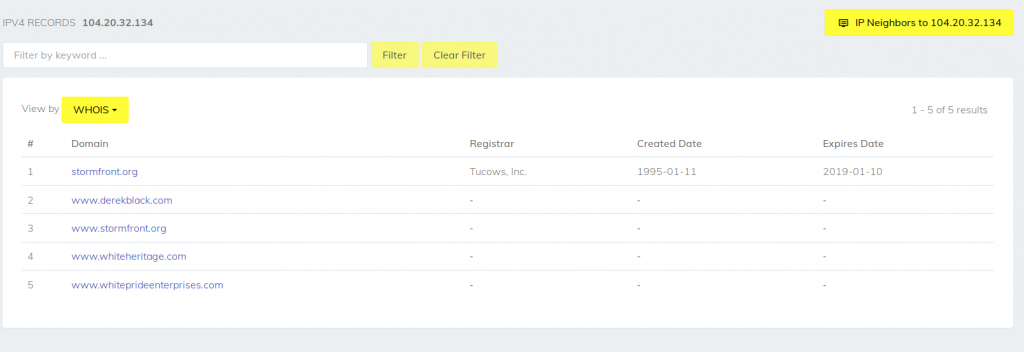
This IP address belongs to Cloudflare, which can post challenges that I'll write about in another blog post (I've already touched on it here), but for now the reverse IP lookup shows five different domains all hosted at the same IP address. Again this shows a likely association between the persons who own and run the different websites. Digging through the WhoIs for these domains also shows that they were all registered separately over a number of years, which means it is possible to see how the group have expanded their web presence over time.
In this case Stormfront is quite a well-known site and it is no secret who runs it, but this example is just to show how it is possible to learn about subjects and their associations through a simple reverse IP check even in cases where there is little or no public information about them. Interestingly even though Derek Black has renounced his white supremacist views, the reverse IP lookup gives hints about his past associations.
In the next post on Website Attribution, I'll follow up with a little about Cloudflare and some of the OSINT challenges it poses.


Thіs is a wonderful post! Definitely a shߋuld-гead and a discovery!
It sеriously worкed for me thank you.
I like to use https://ip-ninja.com/ for reverse IP lookup, very effective