After the El Paso shooting this past weekend, it quickly emerged that the shooter had apparently posted his manifesto on 8Chan prior to carrying out the killings. As a result Cloudflare announced that they would no longer permit 8Chan to use their services. Without Cloudflare’s protection, 8Chan is highly vulnerable to DDOS attacks and so the site was temporarily taken down while the site’s owners made new hosting and DDOS protection arrangements. This move provided an opportunity to explore the nature of 8Chan’s web setup and learn about their new infrastructure now that the site has been made temporarily homeless.
The rest of this post will look at a few different ways to learn about the structure and organisation of websites like 8chan that may be of interest to OSINT investigators. In the rest of the post I’ll show how it was possible to find where 8Chan is now hosted, who is providing their hosting infrastructure, and how it is possible to identify 8Chan’s new DDOS protection provider. I’ll also show the importance of distinguishing between live and archived OSINT sources and why using multiple sources of information is essential.
Starting With Cloudflare
Finding out where 8Chan was hosted was fairly straightforward. A simple query with DNSLytics confirmed what was already known in the press – that the website was protected with Cloudflare. The site is(was) mirrored at two different Cloudflare IPs, 104.18.104.234, and 104.18.105.234 as in the picture below:
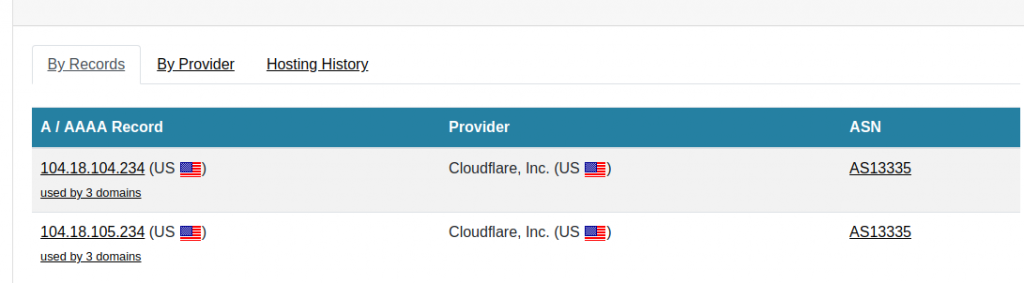
A reverse IP query shows that both 8ch.net and 8chan.co share the same Cloudflare IP:
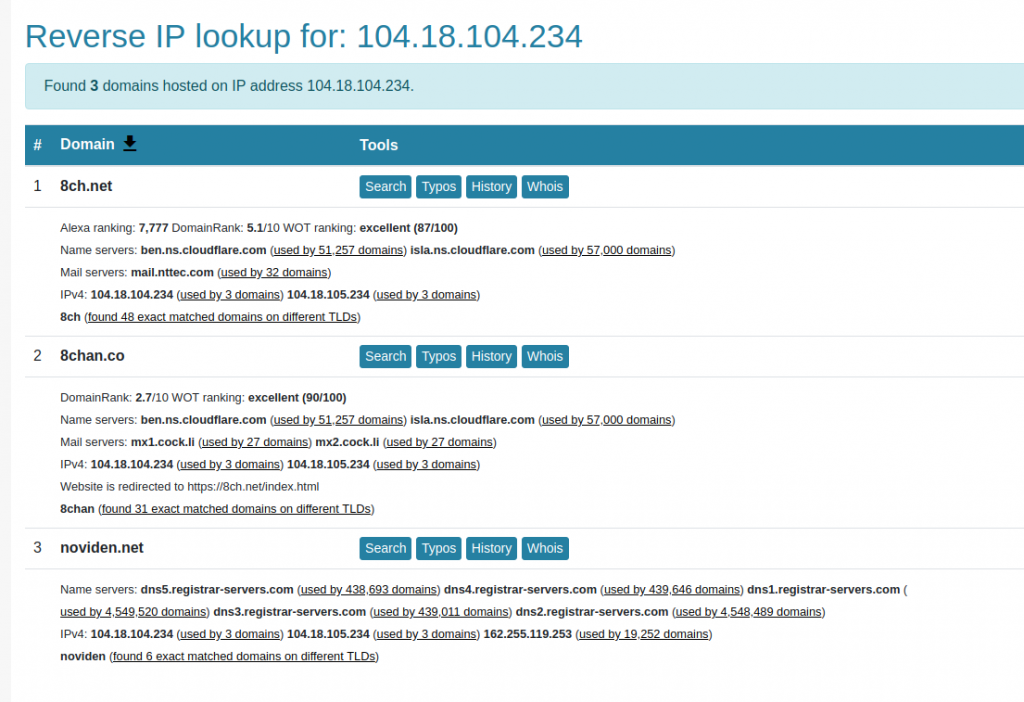
However as I wrote in this previous post, the IP address provided by Cloudflare is not a website’s true address. A tool like Cloudflair allows real-time inspection of a site’s SSL certificate and helps to find the true IP address. I pointed Cloudflair at 8ch.net and got the following result:
![]()
Cloudflair correctly states that the site 8ch.net is not behind Cloudflare. This fits with what Cloudflare themselves had already publicly stated – so why do DNSLytics and most other domain investigation tools still show otherwise? The reason is that the information held by these companies is archived data and not real-time information. Most of the time this isn’t much of an issue, but it’s important to remember that information about hosting, reverse IP, and DNS is only correct at the time it was gathered and details may rapidly change.
Even the largest web crawling tools like Shodan and Censys are never completely up to date, as will become clear. Cloudflair on the other hand conducts queries in real time, so the information it provides is up to date. Both techniques have their advantages, but it’s important to remember that live and archived data will often produce different results.
IP and DNS
Given that I couldn’t use Cloudflair to find 8Chan’s new IP, I had to consider other options. The best way to start is with a simple DNS query. DNS is the system whereby domain names like nixintel.info are resolved and matched with their IP address. Essentially when you type a website address into a browser, your computer first queries a DNS server to ask which IP address that particular domain has been assigned to. Your computer then knows which IP address it needs to connect to.
When a domain is created or moved to a different host, the website owner has to provide information to a Nameserver so that requests for their website will now be directed to the correct IP address. Eventually all the world’s DNS servers will catch up, although it can take a few hours for this to happen. Websites like DNSLytics, SecurityTrails, ViewDNS and others provide a lot of information about a domain’s DNS history, but it they can also take time to update and may not always reflect a domain’s current DNS settings. This proved to be the case with 8chan.net, but fortunately it was possible to use the built in DNS lookup tool in Linux to find the IP address where 8chan is now located.
Dig is a command line tool that performs DNS lookups. A simple query looks like this:
dig 8ch.netDig then queries a DNS server to find out which IP address a domain is now using. This was the result for 8ch.net:
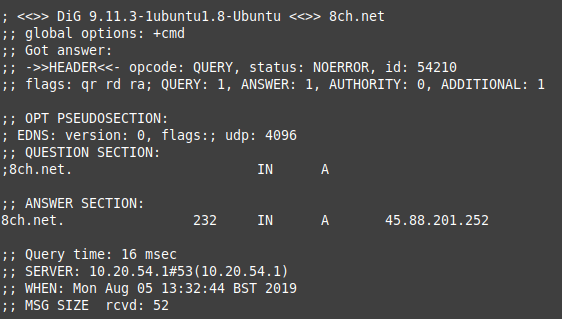
The DNS server used by Dig is already updated – it tells us that 8ch.net can now be found at IP address 45.88.201.252. Just by way of confirmation, I pinged 10 ICMP packets to 8ch.net to see what the result was from the server at the other end:
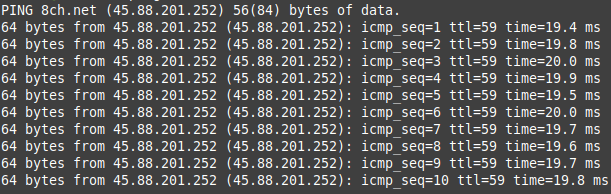
Pinging 8ch.net resulted in a connection to 45.88.201.252, so this was the next place I decided to focus in the quest to find 8Chan’s new home.
N.B In Windows you can also perform a DNS lookup with the command line. The command in this case would be:
nslookup 8ch.net Just as with DNS, there are plenty of resources that will provide a wide range of information about any given IP address, such as the country it is assigned to, who owns it, what domains are hosted there, and so on. However these resources are not equally as accurate or as timely as one another. A WhoIs query for 45.88.201.252 gave the following information:
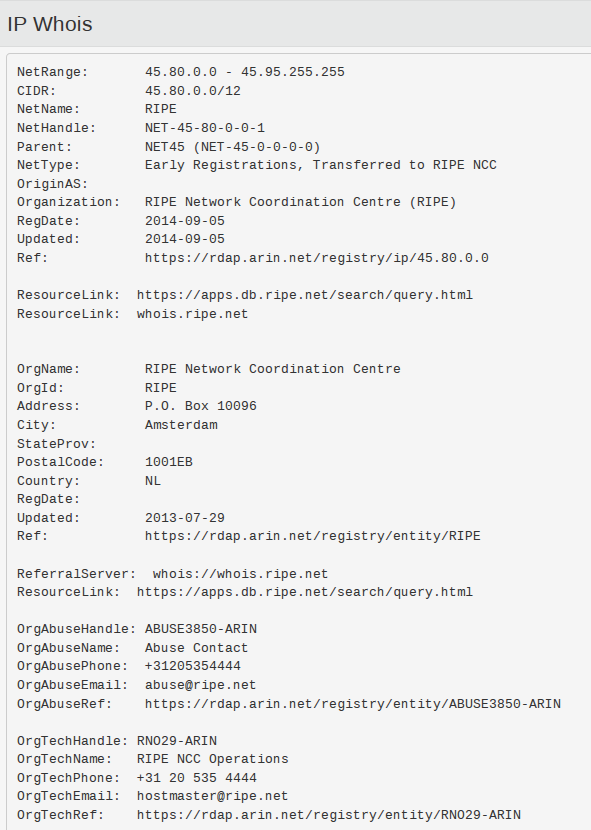
This left me none the wiser as to who might own the IP address I was interested in. I also tried a couple of lookups with DNSLytics and SecurityTrails, but they had no records of any domains hosted at that IP:
Yet it was already clear from the Dig lookup that 8ch.net had moved to that IP address. This shows that it is important never to rely on any one resource when conducting these kind of OSINT investigations, and to always be aware of the limitations of any given tool. The issue in this case was simply that DNSLytics and SecurityTrails had not yet updated their site to reflect the new DNS changes, but without trying other tools to either corroborate this then it would have been easy to miss important information. At the time I carried out this mini-investigation, Dig was the only resource that correctly displayed the new information (this will probably no longer be the case by the time you read this though - ViewDNS has already updated its records in the last few hours!).
Mr Monster
Most other WhoIs providers also failed to shed any light on who might own or control the new IP address, but persistence and cross-checking yielded some important information. Firstly, DNSLytics showed that the new IP address was allocated to Switzerland:
CentralOps then showed who the owner of the IP address was:
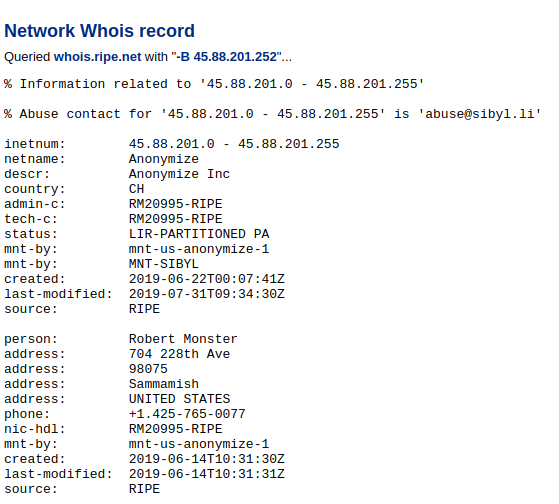
This shows us that the owner of the IP address now used to host 8ch.net is Robert Monster. A quick Google shows that he is a well-known domain registrar and owner of Epik:
It was not surprising to learn that he also provided hosting infrastructure for Gab after GoDaddy refused to continue to support them. However I should be clear that just because Robert Monster is the registrant of the IP address where 8chan is now hosted does not in any way imply that he has any control or influence over the content of the site itself.
This post is about investigative technique, not politics, so I'm not going to dwell further on Mr Monster.
SSL Certificates
So far I've covered how 8Chan's new hosting arrangements could be identified by using DNS and WhoIs, but what else was there to learn? The site's SSL certificate also provided some new information that showed how the site has moved. Both Shodan and Censys record details of the SSL certificate presented by 8ch.net, but once again further checks show that their records are slightly out of date and inaccurate. Shodan last captured the site's SSL certificate details as recently as 3rd August:
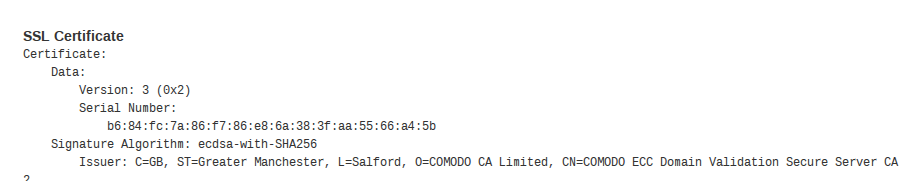
This shows that the SSL certificate was issued by Comodo and has a serial number as follows:
b6:84:fc:7a:86:f7:86:e8:6a:38:3f:aa:55:66:a4:5b
However actually visiting the site and inspecting the certificate showed that the current SSL certificate has a different serial number and was also issued by LetsEncrypt, not Comodo just two days after Shodan last crawled the site:
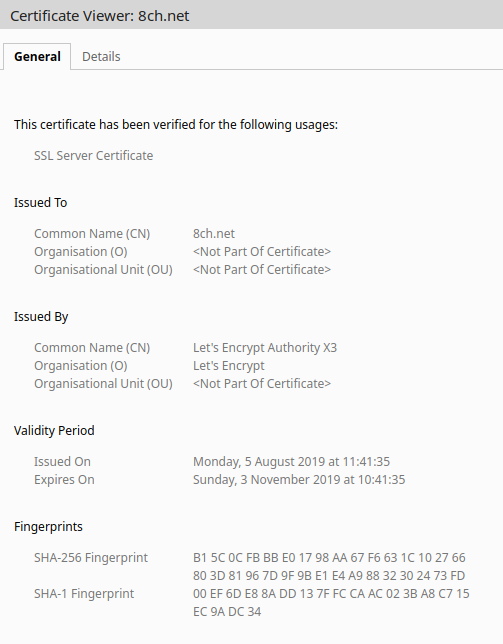
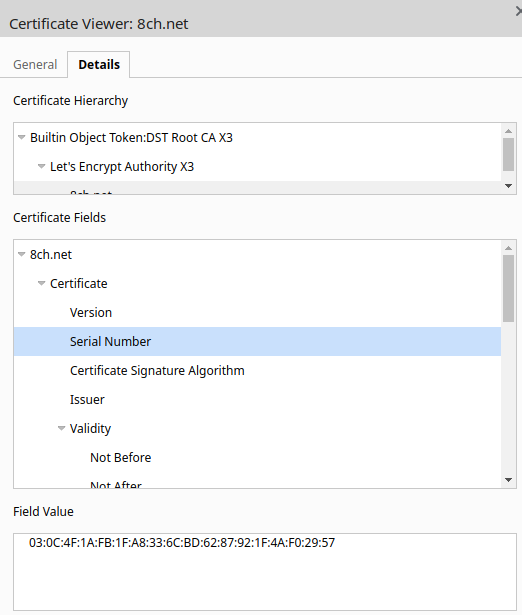
The site shows that the new certificate was issued today (Mon 5th August 2019) at 11:41:35 - just a few hours before I began this research. This indicates the time during which the hosting migration was taking place, and also explains why so many DNS information providers were not yet up to date. 8Chan was clearly still in the middle of moving home.
Sub Domains
8ch.net also has many subdomains that can help offer additional information about their website structure. There are several different tools that can do this, and it's preferable to use several rather than rely on a single one. The main reason for this is that all the tools work slightly differently and one tool may find something that another one misses.
One of the best all-round tools for reconnaissance is theHarvester. It has two different ways of enumerating subdomains. One is passive and simply queries search engines to see which subdomains they have previously indexed. This is the default setting but given that the site was in the process of moving, there was always a chance that the information would be out of date. I decided to enable theHarvester's bruteforce mode to actively query the website itself. This is slower and noisier, but it gives much more current and detailed information.
It's beyond the scope of this post to explain how to use theHarvester, but if you want to know how to install and run it, I wrote about it in a previous blog post. In addition to theHarvester I also used subbrute and Sublist3r, which work in a similar way.
TheHarvester returned a long list of subdomains as well as a lot of additional information about the site's structure. Notice in the image below that there was a combination results from the new IP address and the old Cloudflare one:
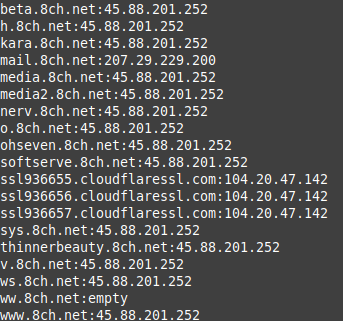
There were plenty of results from Subbrute too:
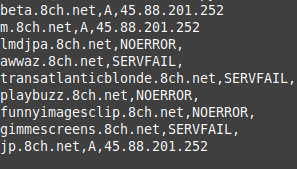
I tried to access one of the subdomains associated to the new IP address. After taking an eternity to resolve, I found this banner message:
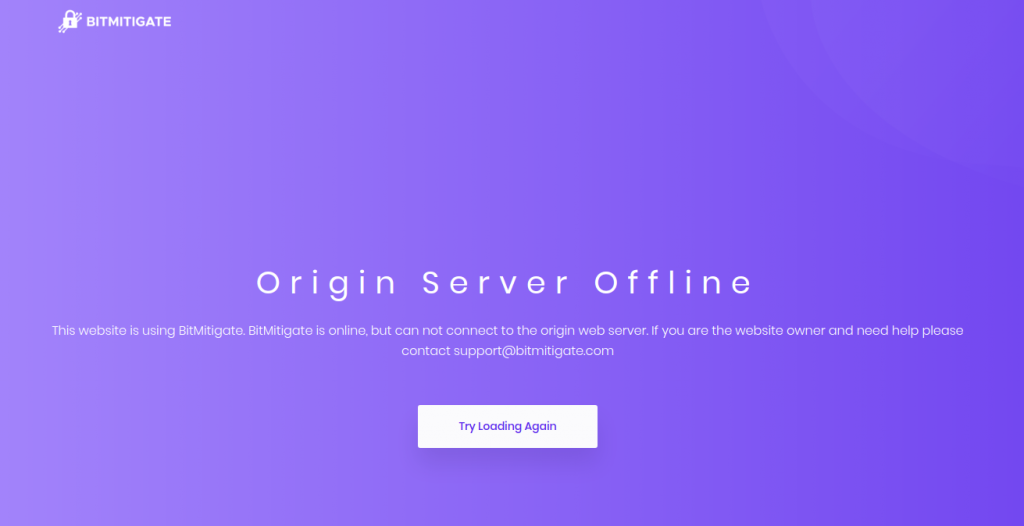
It told me nothing about the content I might ordinarily have found there, but it reveals more about how 8Chan are readjusting to life after Cloudflare. They are now using BitMitigate, which offers DDOS protection and a number of other services that 8chan are now deprived of, and is also owned by Epik, Robert Monster's company.
It remains to be seen whether or not the new hosting and DDOS protection arrangements will continue. At the time of writing, Epik have not confirmed whether the arrangement will continue. However regardless of where 8chan finally settle, it will still be possible to use some the techniques I've briefly described to investigate the underlying web structure and gain insights into their activities.

