Identifying and tracing a person’s footprints across the internet usually involves researching usernames across a wide variety of different platforms. There are many tools available to do this, but I’m a big fan of Sherlock for conducting quick and accurate username searches. Compared to some of the web-based alternatives like KnowEm and Namechk it returns a lower rate of false positives and has useful extra features like being able to run over TOR and allowing results to be easily exported to CSV file for further analysis.
Getting Started
Sherlock is a Python program that runs easily in Linux. It requires Python 3.6 or higher to run so you might need to update your version of Python first. I’ve used Sherlock in Linux Mint 19.1 and also in Kali and it’s quick to set up and simple to use without any glitches. Here’s a quick guide to how to install and use it.
Clone the repository:
$ git clone https://github.com/sherlock-project/sherlockChange to the newly-created Sherlock directory:
$ cd sherlockMake sure you have pip3 installed. If not, install it first:
$ sudo apt install python3-pipThen check the pip version:
$ pip3 --versionYou should get the following output:
pip 9.0.1 from /usr/lib/python3/dist-packages (python 3.6)
Install the necessary requirements for Sherlock:
$ pip3 install -r requirements.txtNow you’re ready to run Sherlock! To run a basic query, use the following syntax within the Sherlock directory:
$ python3 sherlock.py TARGET_USERNAMETo make life a little simpler, create an alias in your .bashrc file. If you’re going to run a script regularly, this makes things a little quicker and less repetitive. This also allows you to run the command from any location without having to move to the Sherlock directory first.
$ nano ~/.bashrcScroll to the end of the file and add the following lines:
#alias to run Sherlock alias sherlock='cd ~/sherlock && python3 sherlock.py'Exit and save with Ctrl+X. You’ll need to close and restart your terminal window for the change to take effect. Now to run Sherlock just enter the following to query a username:
$ sherlock TARGET_USERNAMENote: Sherlock requires Python 3.6 or higher to run. Check your version of Python3 by typing python3 --version in the console. If your version is too old, you can update to Python 3.6 by following this guide. To run the commands as above just replace python3 with python3.6 and it’ll work fine.
What does Sherlock do?
Sherlock queries dozens of different websites to see if any user account for that site matches the username that you’re researching. It’s a very quick and very efficient way to identify other platforms the person is using that you might not find otherwise. Apart from the obvious platforms like Twitter, Facebook, and Reddit, it looks for matches on gaming sites like NameMC, Steam, and Roblox, coding sites like Codeacademy, GitHub, and Gitlab, and dozens of others. Apart from the speed of the searches it carries out, the rate of false positives is very low compared to other tools. I found Sherlock consistently returned false hits for Wikia, but not for any other sites. If you’ve previously used sites like Knowem, or Usersherlock, you’ll appreciate how fast, comprehensive and accurate Sherlock is.
Example Usage
To use Sherlock (assuming you’ve set up the bash alias as above), the format to query a username is simple:
$ sherlock USERNAME Sherlock also allows you to query multiple usernames at once:
$ sherlock USERNAME1 USERNAME2 USERNAME3Or you can query a preloaded JSON file:
$ sherlock -j JSON_FILE_NAMEAnd you can also export the results to a csv file for further work:
$ sherlock USERNAME --csvFor an example username I chose opt1cz. Opt1cz was a UK hacker who was identified by Brian Krebs last year after he DDOSed Protonmail. He’s now in prison but his footprints are still all over the internet. Sherlock quickly finds a large number of matching profiles. Let’s see Sherlock in action:
$ sherlock opt1czIn less than ten seconds, we have multiple positive hits:
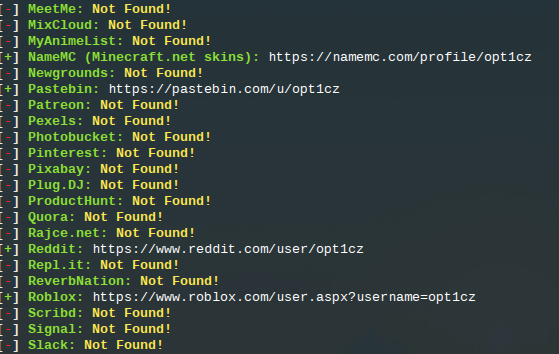
There’s the usual false positive for Wikia, but the rest all link to genuine opt1cz profiles, although of course you’d always need to further work to verify that they were all the same person.
All the blank results are a bit messy, so by adding the parameter
--print-foundto our search we make sure that only positive results will be returned. We will also export the results to a CSV file for further analysis:
$ sherlock opt1cz --print-found --csvThis gives a much neater result:
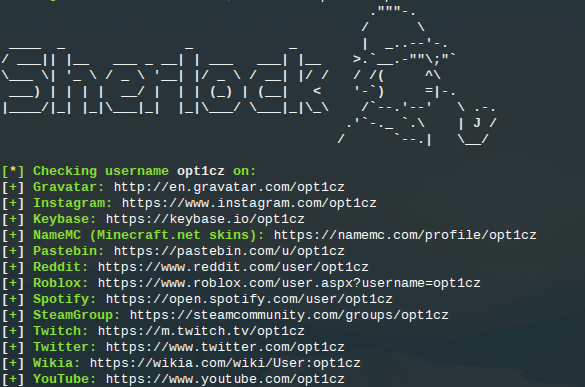
So you can see that Sherlock is very fast, has a high degree of accuracy, and is also flexible with output type. But how does it compare to other username search tools?
Comparison With Other Tools
I conducted the same search for opt1cz on other popular username search platforms. It isn’t an exact scientific test because not all the tools search the exact same websites, but even so there’s a marked difference in performance.
The benchmark set by Sherlock for the test shown above was: Sites scanned: 136, positive hits: 12, false positives: 1.
Sites scanned: 98
Error messages: 8
Positive hits: 8
False positives: 21
Sites scanned: 54 (including some domain availability checks)
Positive hits: 5
False positives: 4 (even more if you count checked domains)
Sites scanned: 25
Positive hits: 0
False positives: 0
This search missed some of the really obvious accounts like Twitter and YouTube. I’m very hesitant to suggest anyone relies a tool that doesn’t find these matches.
Sites scanned: Unknown
Positive hits: 2
False positives: 3
Sites scanned: 25 (most common social media sites only – they do have the option to scan across 500 different sites/brands)
Errors: 1
Positive hits: 4
False positives: 4
Conclusion
So you can see that while Sherlock does not have the instant accessibility of a username search website, it is much faster and more accurate than most of the username checking resources that are frequent favourites in the OSINT community. It’s definitely one to add to your research toolbox!

Pingback: Best OSINT Resources for E-mail Addresses - X-ray Blog
Pingback: Snapchat Reverse Username Lookup Guide 2024