WordPress is the base that 35% of the world’s websites are built on. If you’re ever going to investigate a website, then it’s really important to be able to know your way around a WordPress setup. In this tutorial I’m going to show how to identify user accounts on a WordPress-based website so that you can find out the usernames of those who run it. This uses a command line tool called WPScan, but if you’re not comfortable with the command line then I’ll demonstrate a web-based tool that can do the same thing, albeit less effectively.
WPScan
WPScan is a vulnerability scanner designed to find information about the setup and configuration of WordPress sites. However for OSINT purposes, we’re really interested in using WPScan to find out who the users of a website are. This not only tells us who might be running a website, but it also identifies usernames that can then be checked across other platforms, or even compiled into e-mail addresses. If a user is identified by WPScan it means that they have published some form of content to the site, which makes for very strong attribution if you can identify who the user is. WPScan is already built into Kali Linux, but if you’re using Windows, Mac OS, or a non-Kali Linux distro then you’ll need to install WPScan first.
Installation & Usage
Linux
Unlike many of the Python-based tools I’ve written about on this site previously, WPScan is written in Ruby. Ruby and its associated package manager RubyGems are not always present in Linux by default, so you’ll need to install it along with a few other dependencies. For Ubuntu, Mint, and other Debian-based distros, simply enter in the console:
sudo apt install ruby-dev zlib1g-dev build-essential
Then to install WPScan simply enter the following:
sudo gem install wpscan
Installation takes a few moments. Once it’s completed, enter the following to check your WPScan installation is working:
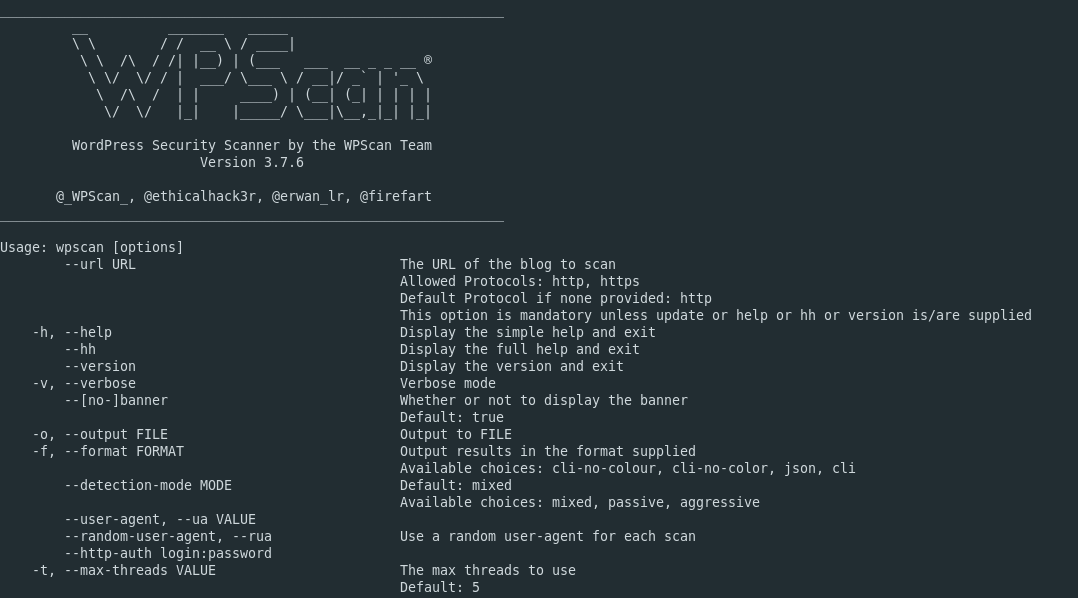
wpscan -h
And you should see something like this:
Windows
To install WPScan in Windows, there’s a detailed guide here. Alternatively you can now run the entire Kali Linux distro from the Microsoft App Store. WPScan and a host of other reconnaissance tools are already included with Kali and once you’ve set it up there’s no need to do anything further.
Identifying A WordPress Site Using BuiltWith
Before scanning a site, how can you even know if it’s using WordPress or not? There’s a few ways to do this, but one of the most useful is BuiltWith. BuiltWith is an excellent OSINT tool in its own right, and even comes with a really handy browser plugin. BuiltWith identifies and lists the underlying technology behind every website that it has indexed. Here’s a snippet of the BuiltWith profile for this website:
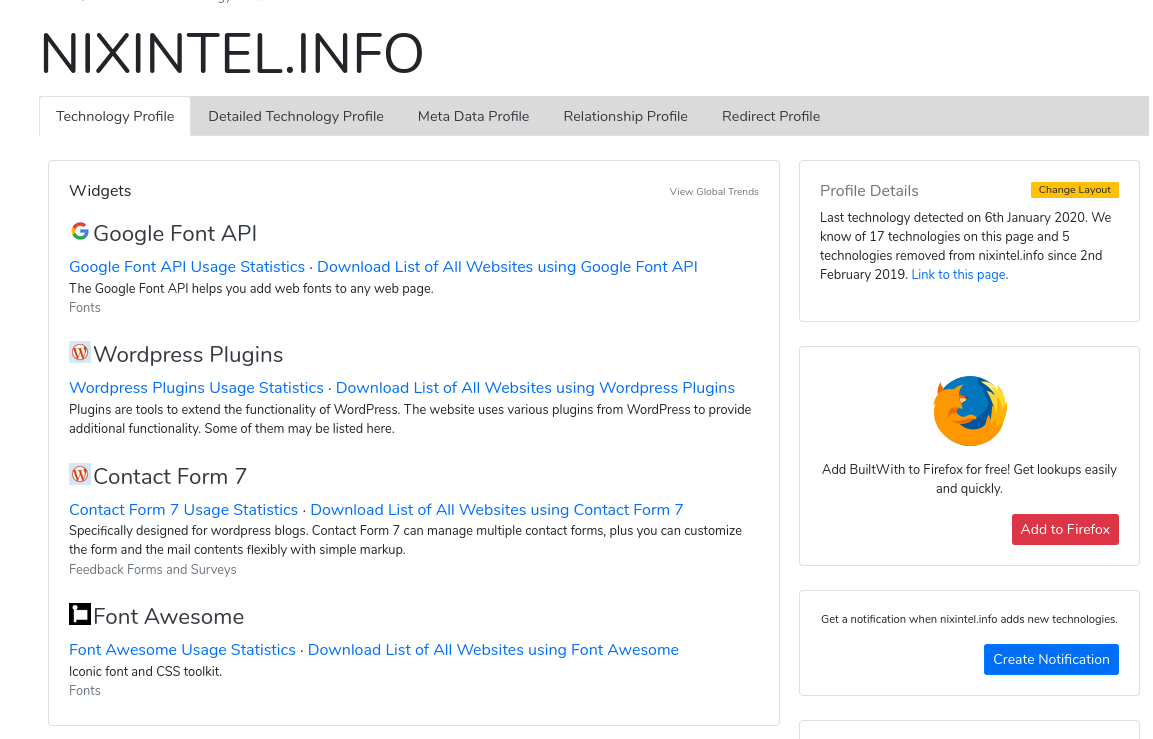
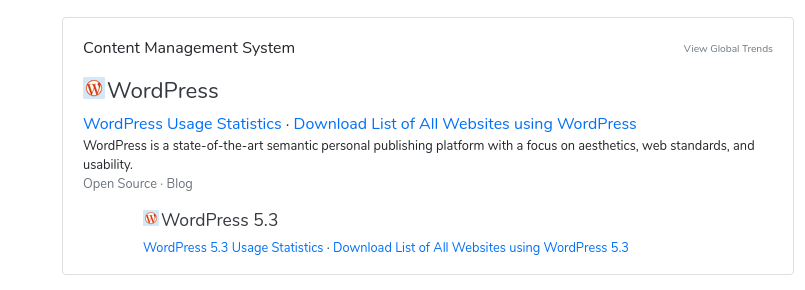
Most websites need some form of content management system, and WordPress is by far the most popular. Once you’ve looked up a website’s profile on BuiltWith, scroll down to the Content Management System section. If it’s a WordPress site, you’ll see something like this:
Usage
WPScan has a wide variety of options, but for OSINT purposes we’re only really interested in the enumeration option. This will tell WPScan to trawl through the website and dig out the usernames of those who have WordPress accounts there. A basic scan syntax looks like this:
wpscan --url https://somewordpresssite.com -e u1-10
–url specifies the URL of the site you want to scan, the -e flag tells WPScan to enumerate, and u1-10 tells it to stop after discovering the first 10 users. We’ll look at some other usage examples as we go through a couple of examples.
A Note of Caution…
WPScan has different levels of scan, with some being more intrusive than others. It’s important to be aware of the risks involved in using a tool like this from a security viewpoint. Firstly, the scan you conduct will be detected in the logs of the server that you target, which means that the server admin could see your IP address, timezone, user agent, and other identifying information. It’s probably not a good idea to start scanning Jihadist websites from your home internet connection. Consider your threat model and take appropriate precautions like a VPN, or running WPScan from a Linux VPS.
Secondly, the more intrusive scans may trigger a server’s IDS (Intrusion Detection System) and you could find that your IP address is blocked from being able to access the site you’re interested in. WPScan will not notify you if this happens. There is also a WordPress plugin called Stop User Enumeration which is specifically designed to prevent these kind of scans from being effective. The worst case scenario is that you end up notifying the site admin and getting yourself blocked from future visits to the site as well.

A Quick Case Study – OSINTCurious

For a real-life example I’m going to point WPScan at the OSINTCurio.us* website to show the different scanning modes and the kind of results WPScan returns. Let’s analyse the site using BuiltWith first:
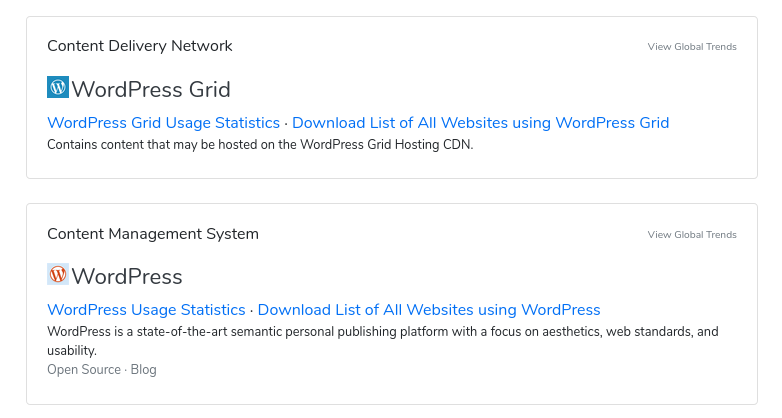
BuiltWith confirms the site is powered by WordPress, so WPScan should be able to tell us which users have accounts there. The first scan we’ll run is a basic scan to identify the first ten users of the site.
wpscan --url https://osintcurio.us -e u1-10
And this returns…an error message saying that the website can’t be found. Why? The most likely is that the site has a least some basic form of protection from enumeration scans. We know it’s there though, so we can try a different approach while still being passive. Adding the –stealthy flag makes our scan a little quieter:
wpscan --url https://osintcurio.us -e --stealthy u1-10
WPScan now fetches a lot of additional information, and it manages to identify several familiar users:
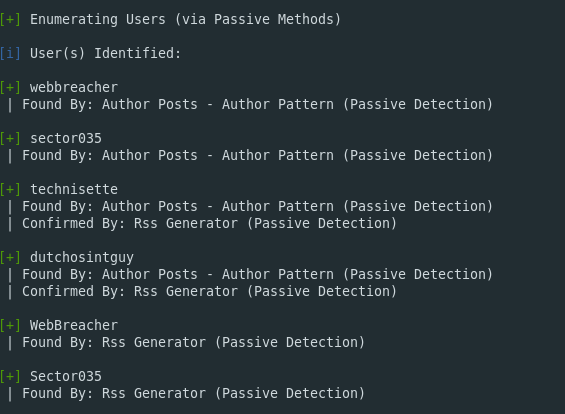
So we know that WebBreacher, Sector035, DutchOSINTGuy and Technisette have user accounts on the OsintCurio.us website – but you probably did not need any complicated tools to know that already. Of course the contributors to OSINTCurious site are not secretive about their project – but this is not always the case.
It is possible to conduct a more aggressive scan, but the flip side of this is that you are more likely to come up against a web server’s security measures. It’s also possible for WPScan not to find every user each time. You’ll notice that Lorand Bodo’s username did not appear in the screenshot above, although it did in an earlier scan.
To scan more aggressively requires tweaking the command a little like this:
wpscan --url https://osintcurio.us -e --rua --detection-mode aggressive u1-10
–rua randomises the user agent, so the scan is less likely to be detected.
–detection-mode aggressive makes the detection mode aggressive!
Running this kind of scan takes longer and brings back more information about the site, although in the case of OSINTCurio.us, it didn’t actually identify user accounts that were not already detected with a passive scan. Every single website is different, and the level of detail returned varies from site to site.
Another Example: Far-Right Blogs
A few weeks ago Lorenzo Romani posted a useful guide to show how it was possible to identify the correct IP address of the Italian neo-fascist blog CasaPoundItalia, even though it was behind Cloudflare, but can WPScan tell us anything else about who runs the site? A quick check shows that this site also runs on WordPress so we can scan it with WPScan to find out who has a WordPress user account there. This scan is passive (the default setting) with user agent randomisation:
wpscan --url https://www.casapounditalia.org -e u1-20 --rua --stealthy
And here are some results:
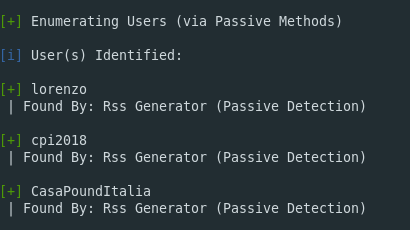
So WPScan reveals three users who have accounts and who have published content to the website.
It would be possible to try and pivot from here and perhaps use a tool like Sherlock to see if these usernames appear on any other websites.
You could even combine these usernames with e-mail tools like Hunter.io or Emailrep.io to see if it’s possible to deduce their email address with the format [email protected]. Where a WordPress-powered site also has its own e-mail server, it’s a fairly reasonable bet that this format will work.
GUI Scanning Tools
WPScan is a powerful OSINT gathering tool if used correctly, but the command line is a little unforgiving if you’re not used to it. There is a browser-based alternative if you’d prefer, although it’s not quite as effective in my opinion.
HackerTarget offers a WordPress enumeration tool similar to WPScan, except that it runs in your browser. By default you can only conduct a passive search and identify the first two users per site. You’ll need to sign up for an account (from $10/month) to get more detailed results.
For some other posts on website attribution, click here.
*OSINTCurious was not harmed during the making of this post, and they were aware in advance that I was going to scan the site.


Hi,
Looks like a good piece, this.
Question: How do I install WPScan on a Mac? Don’t see instructions for that.
Cheers,
You need to install brew on your mac first and then install WPScan.
There’s a walkthrough here:
https://blog.sucuri.net/2021/04/how-to-install-wpscan-wordpress-vulnerability-scan.html
Pingback: PAPERWALL: Chinese Websites Posing as Local News Outlets Target Global Audiences with Pro-Beijing Content - Citizen Lab - GurNews
very info article about WP scan.
Scaning WordPress Website is very Crucial
here’s a full tutorial for WP Scan
https://lostinpress.com/how-to-use-wpscan/